Truist Bank, a leading U.S. commercial bank, has confirmed a breach of its systems resulting from an October 2023 cyberattack. This confirmation follows the appearance of some of the company’s data for sale on a hacking forum.
Based in Charlotte, North Carolina, Truist Bank was established through the merger of SunTrust Banks and BB&T (Branch Banking and Trust Company) in December 2019.
As one of the top-10 commercial banks in the United States, Truist holds total assets of $535 billion. The bank provides a comprehensive range of services, including consumer and small business banking, commercial banking, corporate and investment banking, insurance, wealth management, and payments.
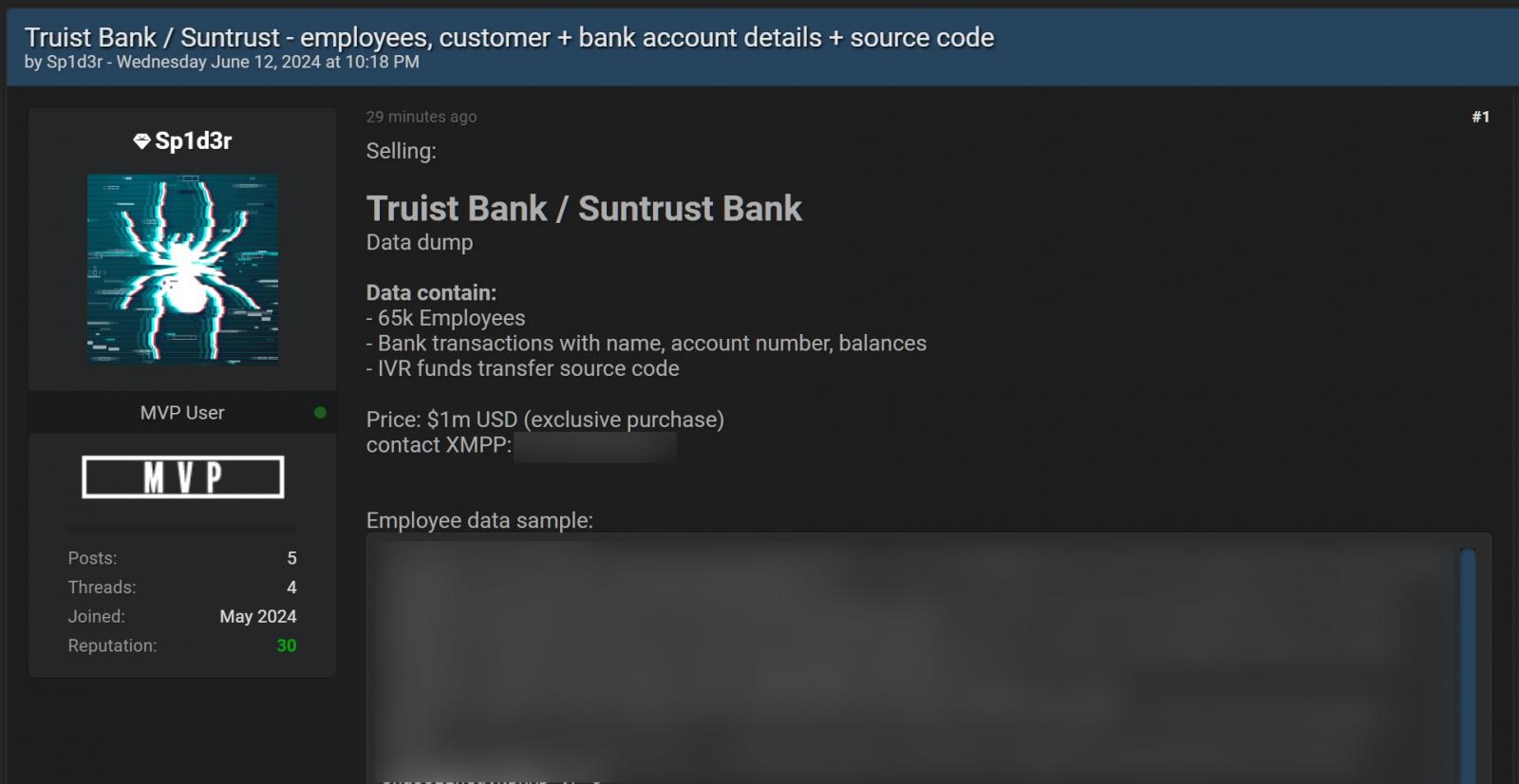
A threat actor known as Sp1d3r is selling what they claim to be stolen data, which includes information on 65,000 employees, for $1 million. This was first identified by DarkTower intelligence analyst James Hub.
Although BleepingComputer could not independently verify these claims, the data allegedly includes bank transactions with names, account numbers, balances, and IVR funds transfer source code.
STOLEN TRUIST BANK DATA UP FOR SALE (BLEEPINGCOMPUTER)
“In October 2023, we experienced a cybersecurity incident that was quickly contained,” a Truist Bank spokesperson told BleepingComputer when asked to comment on the threat actor’s claims.
“In partnership with outside security consultants, we conducted a thorough investigation, implemented additional measures to secure our systems, and notified a small number of clients last fall. When asked if this was connected to the ongoing Snowflake attacks, the spokesperson said, “That incident is not linked to Snowflake. To be clear, we have found no evidence of a Snowflake incident at our company.”
“We regularly work with law enforcement and outside cybersecurity experts to help protect our systems and data,” the Truist Bank spokesperson added.
“Based on new information from the ongoing investigation of the October 2023 incident, we have notified additional clients. We have found no indication of fraud arising from this incident at this time.”
The same threat actor is also selling data stolen from the cybersecurity company Cylance for $750,000. This includes databases allegedly containing 34,000,000 customer and employee emails, as well as personally identifiable information belonging to Cylance customers, partners, and employees.
Cylance confirmed the legitimacy of these claims, stating that it’s old data (from 2015-2018) stolen from a “third-party platform.”
Sp1d3r also previously listed 3TB of data belonging to automotive aftermarket parts provider Advance Auto Parts on the same hacking forum. This data was stolen after breaching Advance’s Snowflake account.
Source: BleepingComputer, Sergiu Gatlan