Cybercriminals are increasingly abusing Cloudflare’s ‘pages.dev’ and ‘workers.dev’ domains, which deploy web pages and facilitate serverless computing, for phishing and other malicious activities.
Cybersecurity firm Fortra reports that abuse of these domains has increased by 100% to 250% compared to 2023.
Researchers suggest that attackers exploit these domains to enhance the legitimacy and effectiveness of their malicious campaigns, leveraging Cloudflare’s trusted branding, reliable services, low usage costs, and reverse proxying options that hinder detection.
Pages abuse
Cloudflare Pages enables front-end developers to build, deploy, and host fast scalable websites directly on Cloudflare’s global Content Delivery Network (CDN).
The platform hosts static sites, supports various modern web app deployment frameworks, and provides default SSL/TLS encryption, ensuring HTTPS connections without additional configuration.
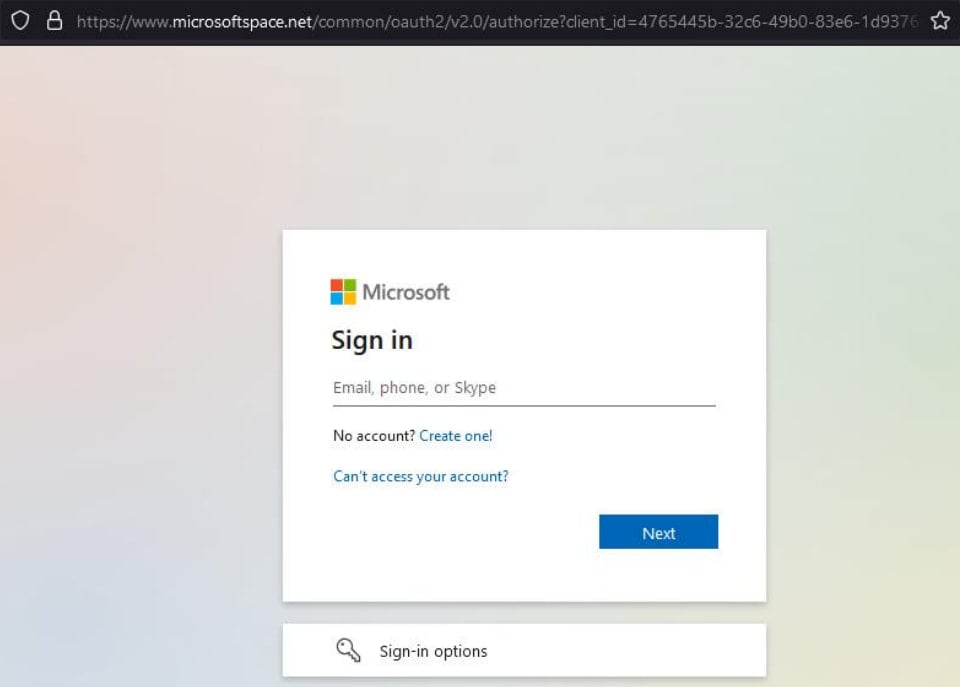
Fortra reports that cybercriminals exploit Cloudflare Pages to host intermediary phishing pages, which redirect victims to malicious sites like fake Microsoft Office365 login pages.
Microsoft 365 phishing page
Source: Fortra
Cybercriminals direct victims to these pages through links embedded in fraudulent PDFs or phishing email bodies, which evade security product detection due to Cloudflare’s strong reputation.
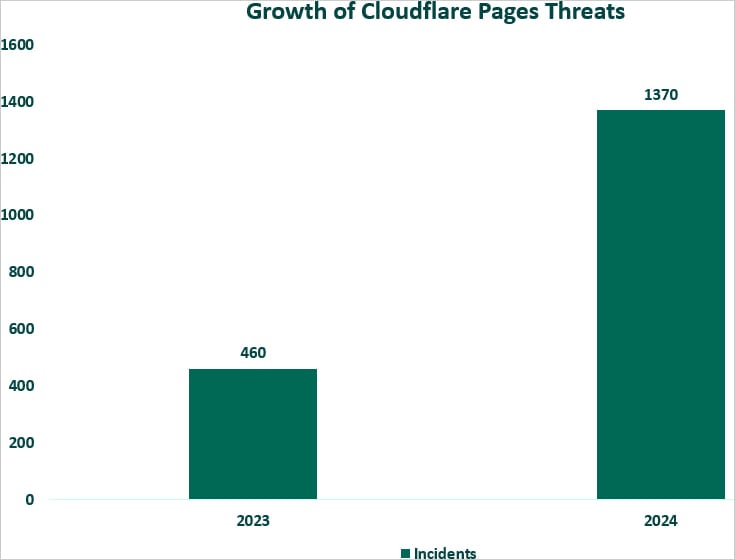
“Fortra’s SEA team has recorded a 198% increase in phishing attacks on Cloudflare Pages, rising from 460 incidents in 2023 to 1,370 incidents by mid-October 2024,” Fortra reports.
“With an average of approximately 137 incidents per month, we expect the total volume of attacks to exceed 1,600 by year-end, marking a projected year-over-year increase of 257%.”
Abuse of Cloudflare Pages in numbers
Source: Fortra
Fortra highlights that threat actors employ the “bccfoldering” tactic to conceal the scale of their email distribution campaigns.
“Unlike the cc field, which displays recipients, bccfoldering hides them by adding recipients only to the email envelope, not the headers,” Fortra explains.
“This tactic allows adversaries to obscure the scale of their phishing campaigns, as concealed recipients make it challenging to detect the full extent of the operation unless the server is configured to reveal them.”
Phishing email containing a link to a Cloudflare Pages domain
Source: Fortra
Workers abuse
Cloudflare Workers Empowers developers to write and deploy lightweight applications and scripts directly on Cloudflare’s edge network, offering a Serverless Computing platform.
Developers use it Legitimately for API Deployment, content Optimization, custom Firewall and CAPTCHA implementation, task Automation, and creating Microservices.
Fortra reports a surge in abuse of Workers, with threat actors using it to carry out Distributed Denial of Service (DDoS) attacks, deploy Phishing sites, inject harmful scripts into victims’ browsers, and Brute-force account Passwords.
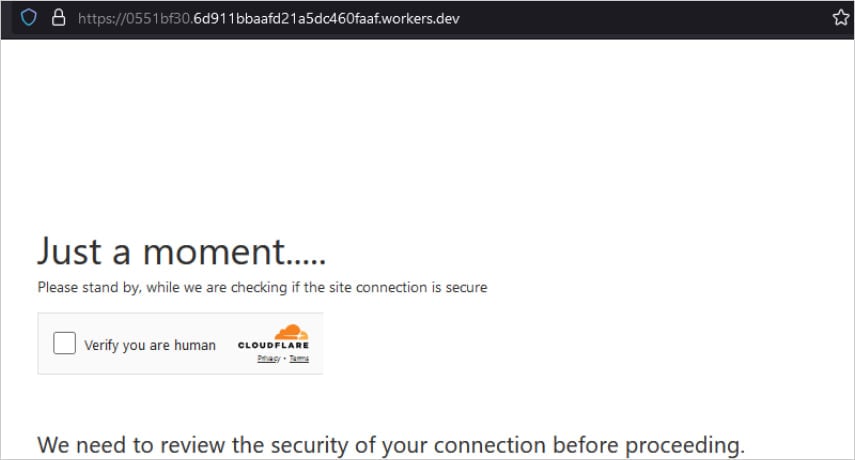
In one instance cited by researchers, Cybercriminals Exploited Cloudflare Workers to host a human Verification step in a Phishing scheme, Enhancing its Legitimacy.
Verification step used in a Phishing campaign
Source: Fortra
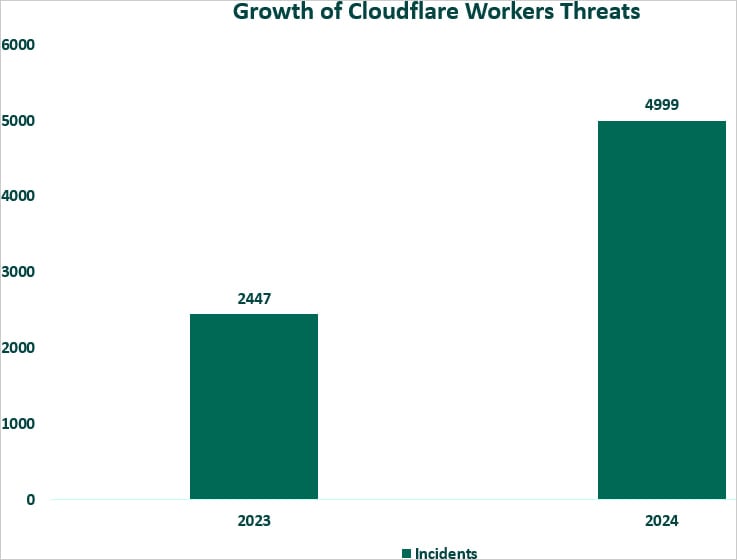
“We have recorded a 104% increase in phishing attacks on this platform [Cloudflare Workers], rising from 2,447 incidents in 2023 to 4,999 incidents so far this year,” Fortra reports.
“With an average of 499 incidents per month, we anticipate the total volume to approach 6,000 by year-end, marking a projected 145% rise compared to the previous year.”
Volume of Cloudflare Workers abuse
Source: Fortra
Users can combat Phishing attacks abusing legitimate services by Verifying the Authenticity of URLs before entering sensitive information.
Enabling additional account security measures, such as Two-factor Authentication, can also prevent account Takeovers even if Credentials are Compromised.
Source: BleepingComputer, Bill Toulas