The Medusa banking trojan for Android has resurfaced after nearly a year of low activity, now targeting users in France, Italy, the United States, Canada, Spain, the United Kingdom, and Turkey.
Since May, new campaigns have been tracked featuring more compact variants of Medusa, requiring fewer permissions and boasting new capabilities aimed at initiating transactions directly from compromised devices.
Known also as TangleBot, the Medusa banking trojan is an Android malware-as-a-service (MaaS) operation first discovered in 2020. It offers functionalities such as keylogging, screen control, and SMS manipulation.
Although it shares its name with a ransomware gang and a Mirai-based botnet for distributed denial-of-service (DDoS) attacks, this Medusa operation is distinct.
The recent campaigns were discovered by the threat intelligence team at online fraud management company Cleafy, who noted that the malware variants are lighter, require fewer permissions, and include full-screen overlaying and screenshot capturing.
The first evidence of the recent Medusa variants appeared in July 2023, according to Cleafy researchers. They observed campaigns that used SMS phishing (‘smishing’) to side-load the malware via dropper applications.
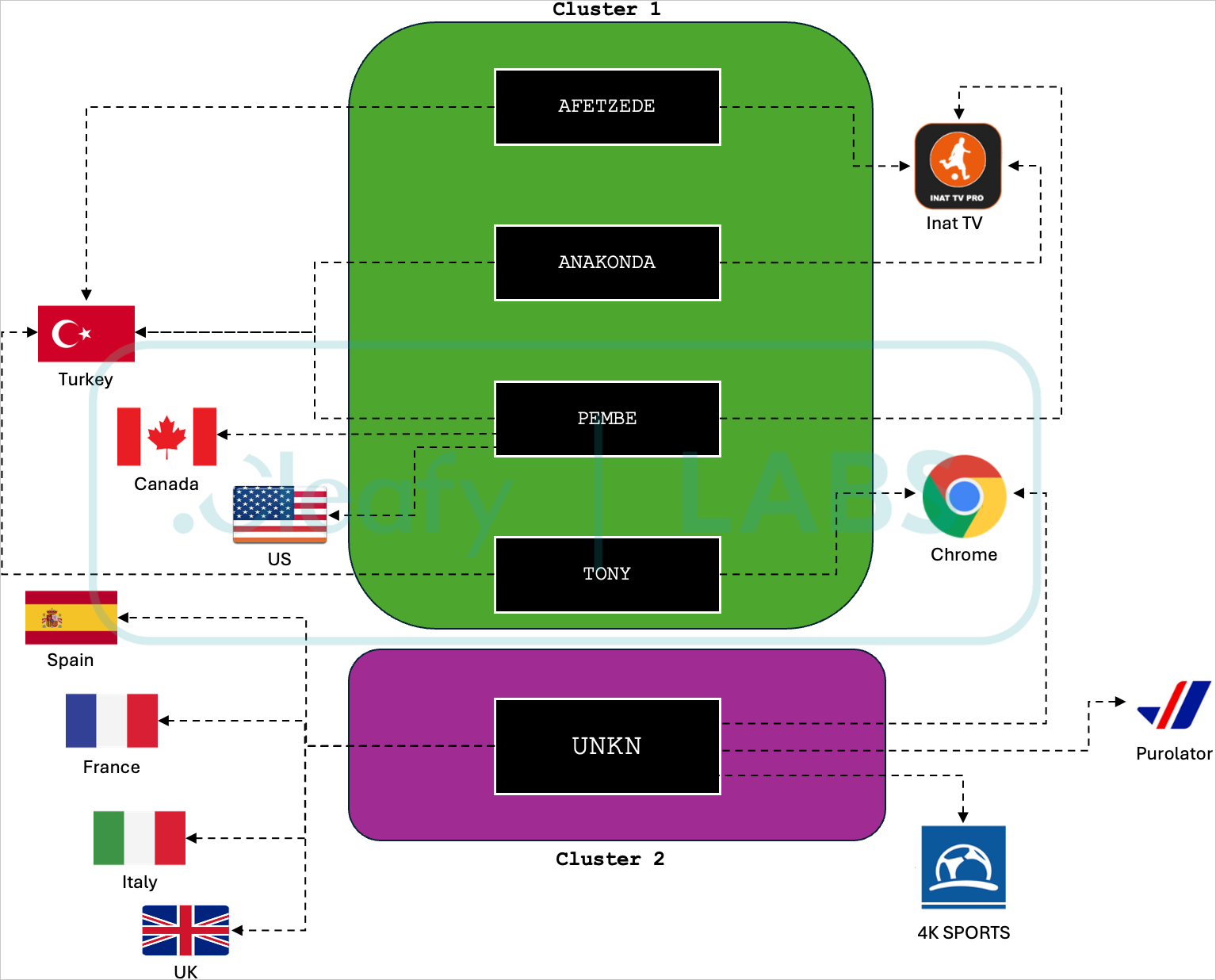
The researchers identified 24 campaigns employing the malware, attributing them to five separate botnets (UNKN, AFETZEDE, ANAKONDA, PEMBE, and TONY) that distributed malicious apps.
The UNKN botnet is operated by a distinct cluster of threat actors, focusing on targeting countries in Europe, particularly France, Italy, Spain, and the UK.
Overview of Medusa botnets and clusters
Source: Cleafy
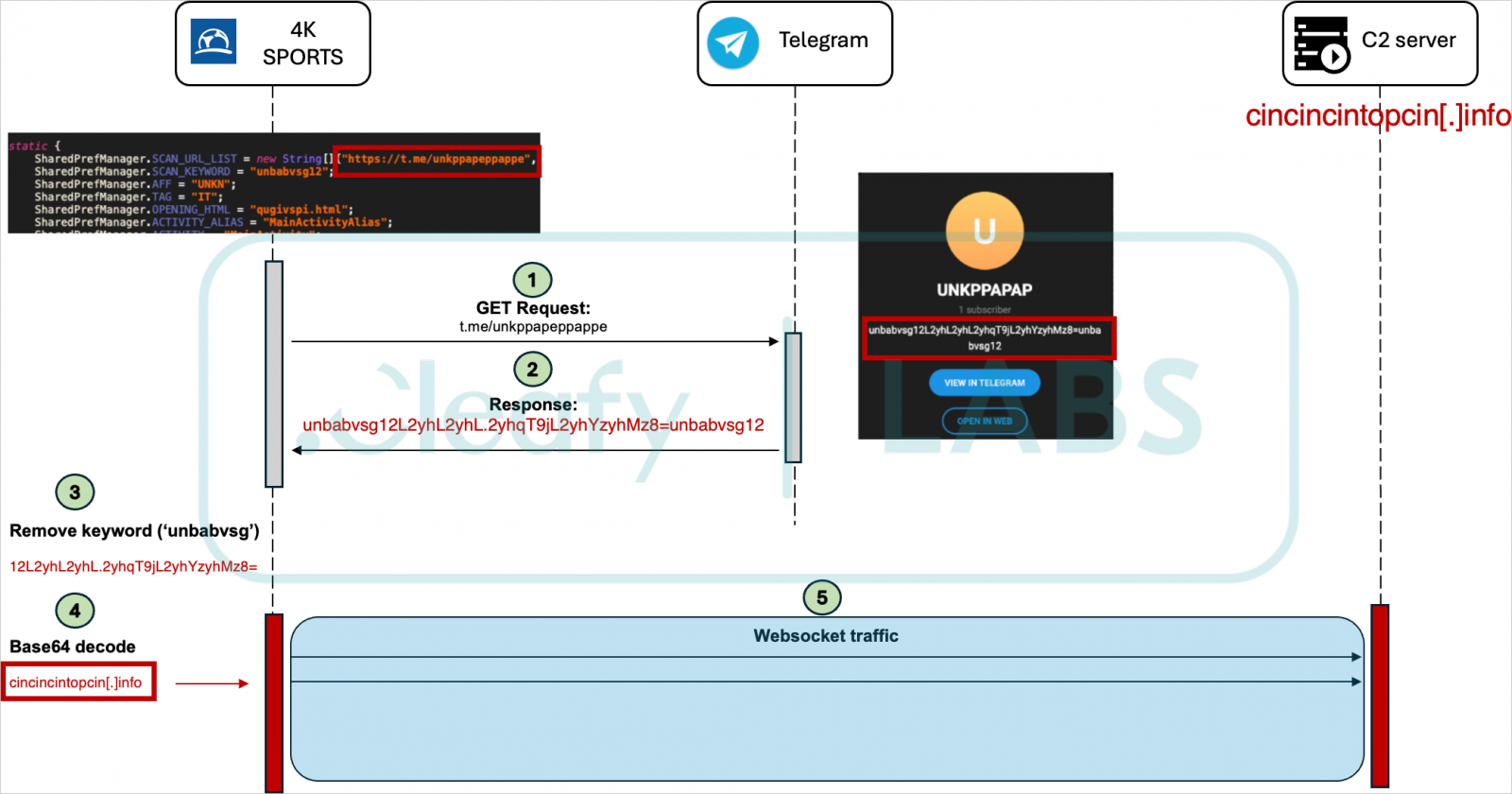
Recent dropper apps used in these attacks include a fake Chrome browser, a 5G connectivity app, and a fake streaming app called 4K Sports. Given that the UEFA EURO 2024 championship is currently underway, the choice of the 4K Sports streaming app as bait seems timely.
Cleafy comments that all campaigns and botnets are handled by Medusa’s central infrastructure, which dynamically fetches the URLs for the command and control (C2) server from public social media profiles.
Retrieving C2 addresses from covert channels
Source: Cleafy
New Medusa Malware variant
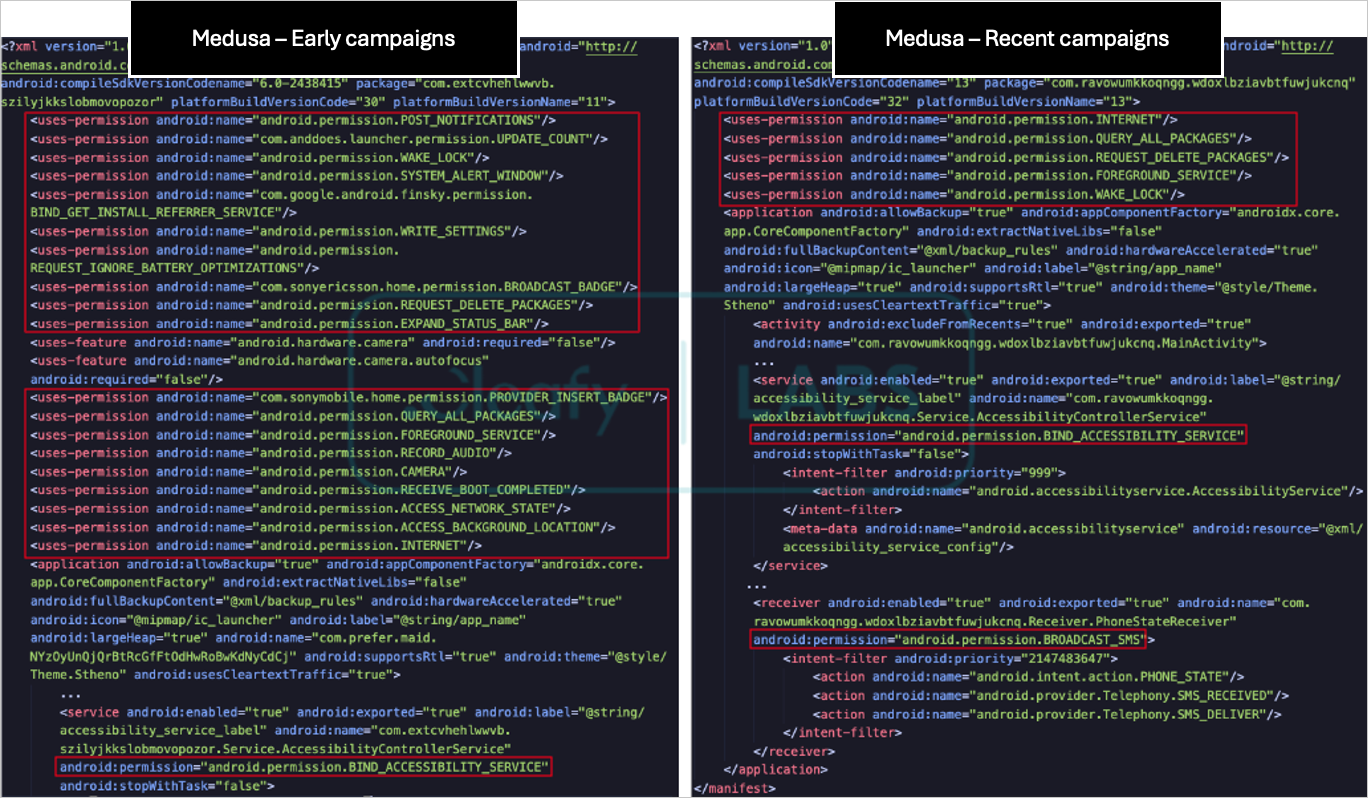
The authors of the Medusa malware have chosen to minimize its footprint on compromised devices, now requesting only a limited set of permissions while still requiring access to Android’s Accessibility Services.
Additionally, the malware maintains its ability to access the victim’s contact list and send SMS messages, a crucial method for its distribution.
Comparison of requested permissions
Source: Cleafy
According to Cleafy’s analysis, the malware authors have removed 17 commands from the previous version and introduced five new ones:
- destroyo: Uninstall a specific application.
- permdrawover: Request ‘Drawing Over’ permission.
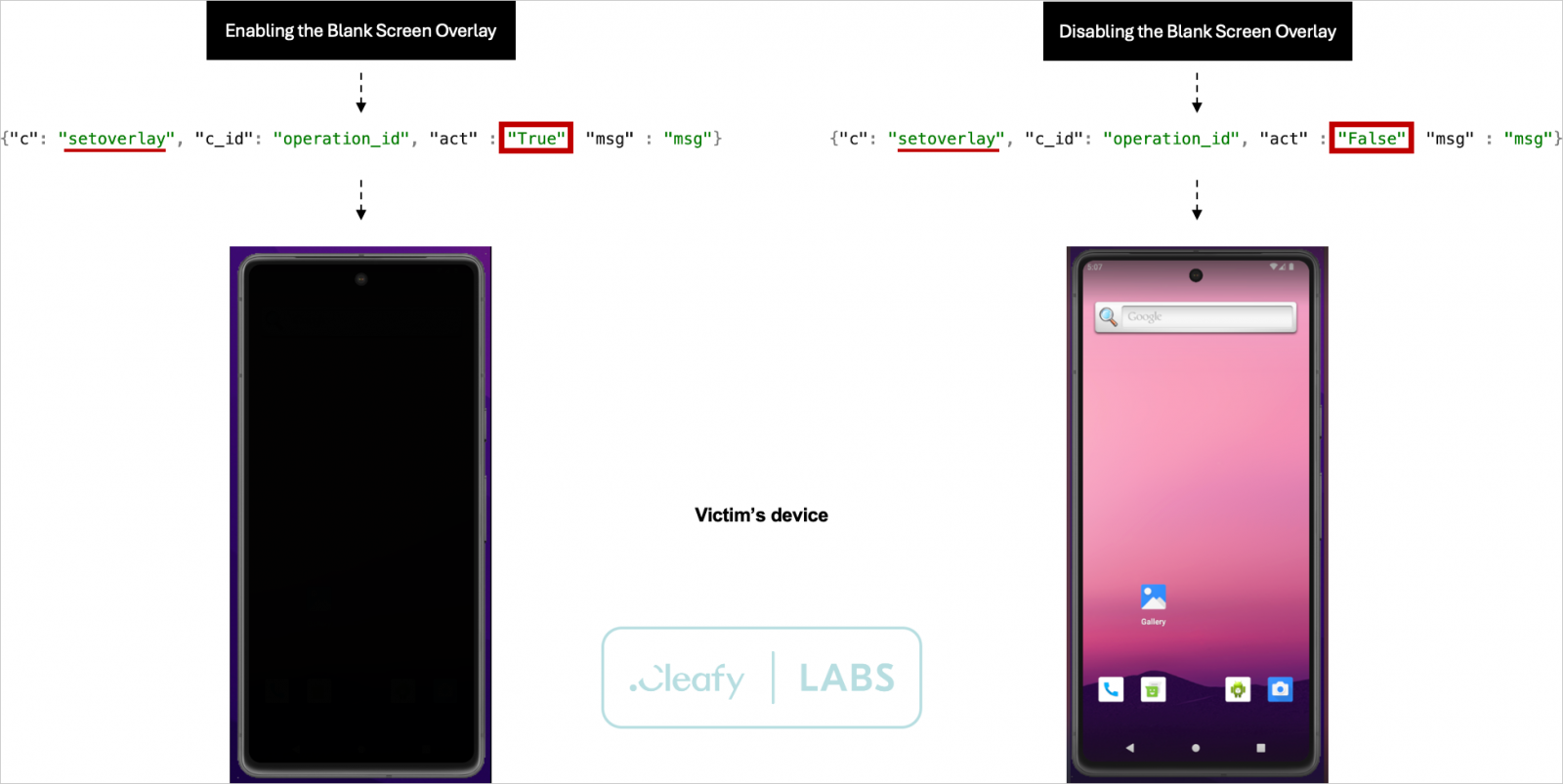
- setoverlay: Set a black screen overlay.
- take_scr: Take a screenshot.
- update_sec: Update user secret.
The ‘setoverlay’ command is particularly noteworthy because it allows remote attackers to engage in deceptive actions, such as making the device appear locked or shut off. This masks malicious activities, including those related to ODF (Overlay and Device Fingerprinting), occurring in the background.
Black screen overlay in action
Source: Cleafy
The new capability to capture screenshots is also an important addition, providing threat actors with a fresh method to pilfer sensitive information from compromised devices.
Overall, the Medusa mobile banking trojan operation appears to be expanding its targeting scope and becoming stealthier, setting the stage for broader deployment and a higher number of victims.
Although Cleafy has not observed any of the dropper apps on Google Play yet, as more cybercriminals join the MaaS (Malware-as-a-Service) ecosystem, distribution strategies are likely to diversify and become more sophisticated.
Source: BleepingComputer, Bill Toulas