A database with more than 350,000 verified Spotify user accounts found on an online server with no password. The list, about 72GB, was found by Noam Rotem and Ran Locar, security researchers at vpnMentor.
According to the researchers, cybercriminals used credential stuffing techniques to compile a database with verified username and password, plus email and country of residence. A total of 380 million (over 72GB) separate records, which were hosted on an unprotected Elasticsearch server.
Credential stuffing, or filling in credentials, is a simple attack in which a cybercriminal attempts to log into multiple systems with the same password that was leaked from a particular service. This only affects people who use the same password for different online services. For example: if you accidentally leak your access credentials for a particular service and you use the same (or very similar) password to log into other websites, apps or systems, cybercriminals may try to use that leaked password to access other services.
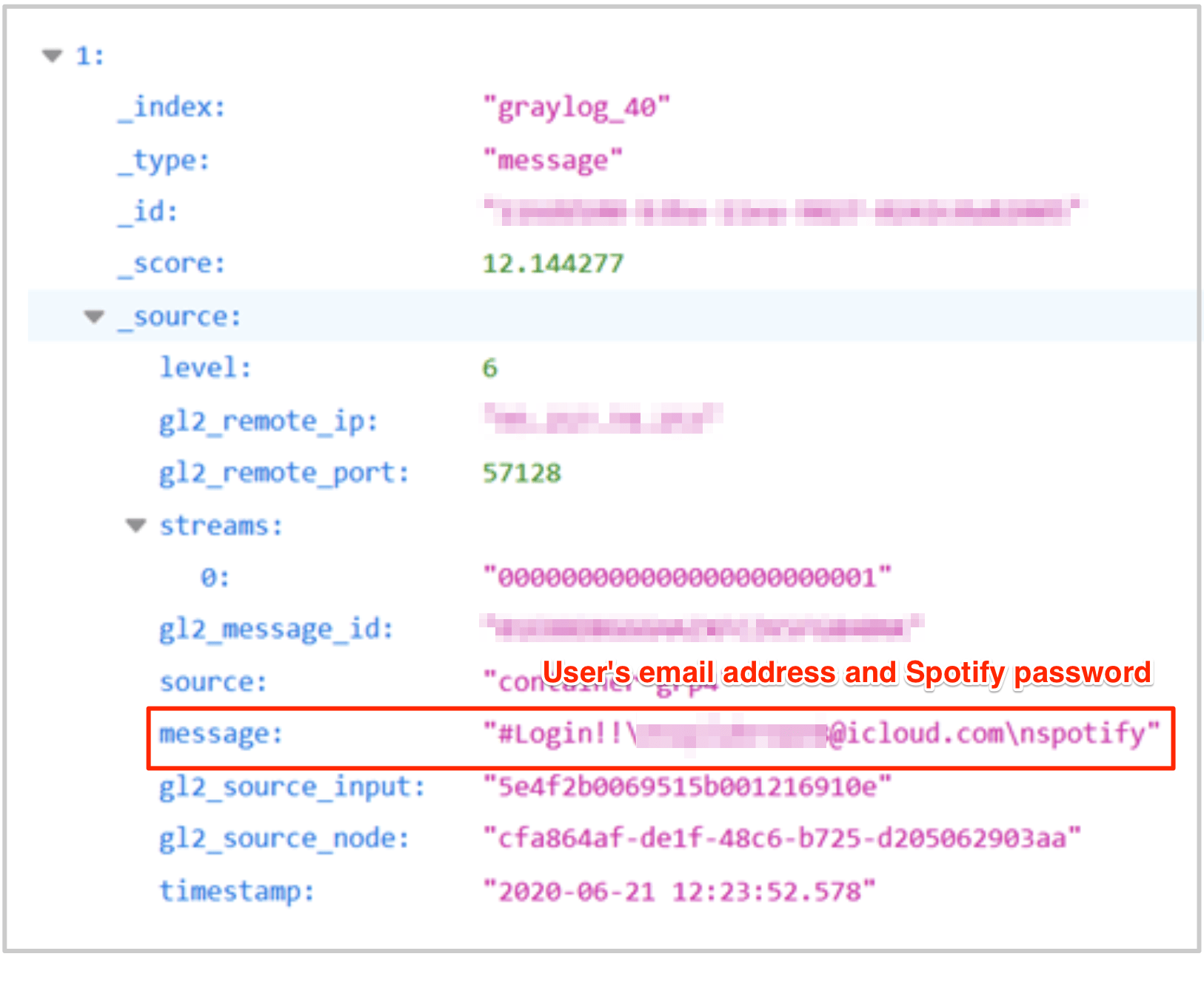
In this case, cybercriminals have appropriated old leaks to build a list of users who use the same password leaked for Spotify. That is, no vulnerabilities were exploited in the Spotify app. The list was built based on other leaks and was found online, without a password, available to anyone with access to the internet.
“The incident did not originate from Spotify. The exposed database belonged to a third party who was using it to store Spotify login credentials. These credentials were probably obtained illegally or potentially leaked from other sources that were reused for credential filling attacks against Spotify, ”say the researchers in a post on the company’s blog.
The researchers report that they have contacted the Spotify, which initiated a ‘continuous reset’ of passwords for all affected users, canceling the exposed information. In addition, this problem is usually not the responsibility of companies, as they cannot control how users create their passwords. “Companies cannot prevent this from happening, as do not control passwords that consumers use (and reuse) online”, Comment the researchers.
The database was found to be completely unprotected and unencrypted in a routine web scan of the company. “We were able to access it [banco de dados] through the browser and manipulate the URL search criteria to expose single index schemes at any time ”.
In the report, the researchers report that there is no way to know who accessed the data and also discuss the potential impacts of an incident like this, which boils down to financial fraud; Identity theft; malware and phishing attacks.
Source: vpnMentor.
See the original post at: https://thehack.com.br/spotify-mais-de-350-mil-contas-foram-encontradas-em-banco-de-dados-desprotegido/?rand=48873