Threat actors known as ‘Stargazer Goblin‘ have established a Distribution-as-a-Service (DaaS) for malware. Using over 3,000 fake GitHub accounts to spread information-stealing malware.
This malware distribution service, named Stargazers Ghost Network, leverages GitHub repositories. And compromised WordPress sites to distribute password-protected archives containing malware. Predominantly, the malware involved are infostealers like RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer.
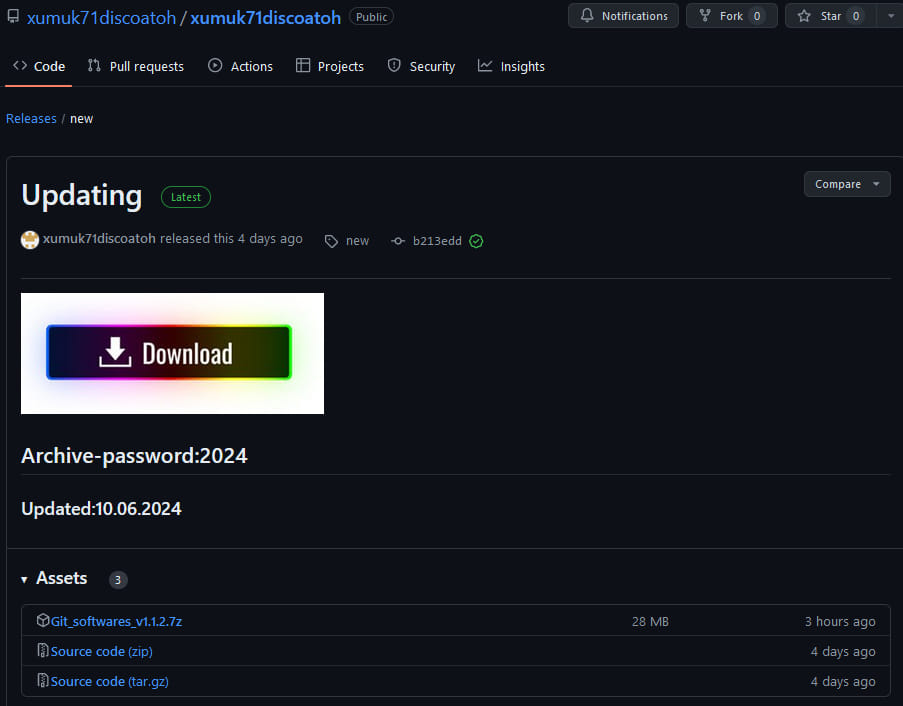
GitHub repository pushing password-protected archive containing malware
Source: Check Point
Given GitHub’s reputation as a trusted platform, users tend to treat it with less suspicion, increasing the likelihood of clicking on links within its repositories.
Check Point Research uncovered this operation, noting it is the first documented instance of such an organized and large-scale scheme operating on GitHub.
“The campaigns conducted by the Stargazers Ghost Network and the malware distributed through this service have been highly successful,” states the report by Check Point Research.
In a short span, thousands of victims unknowingly installed software from seemingly legitimate repositories. The targeted phishing templates used by the threat actors enable them to infect victims with specific profiles and online accounts, making these infections particularly valuable.”
GitHub ‘ghosts’ spreading malware
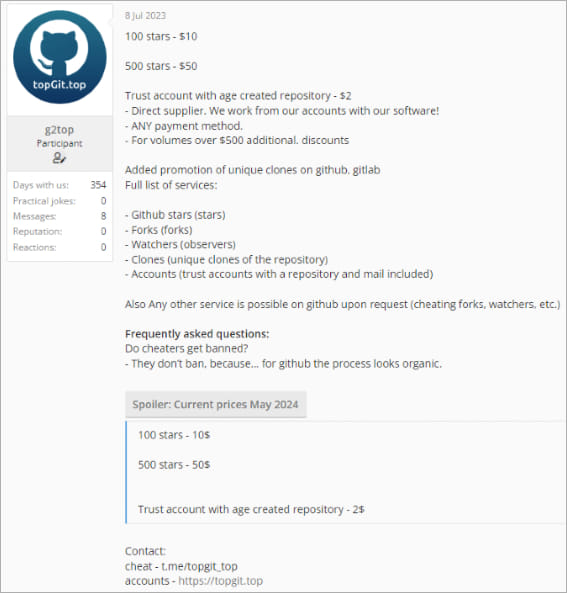
The creator of the DaaS operation, Stargazer Goblin, has been actively promoting the malware distribution service on the dark web since June 2023. However, Check Point indicates that evidence suggests activity since August 2022.
Threat actor’s ad on the dark web
Source: Check Point
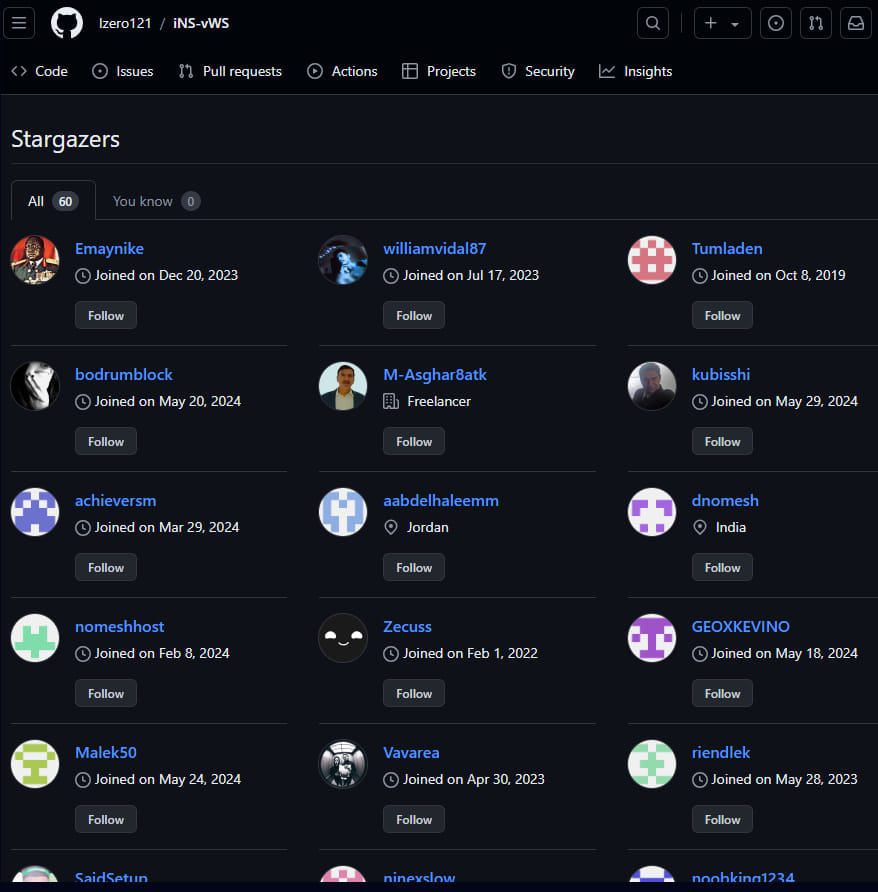
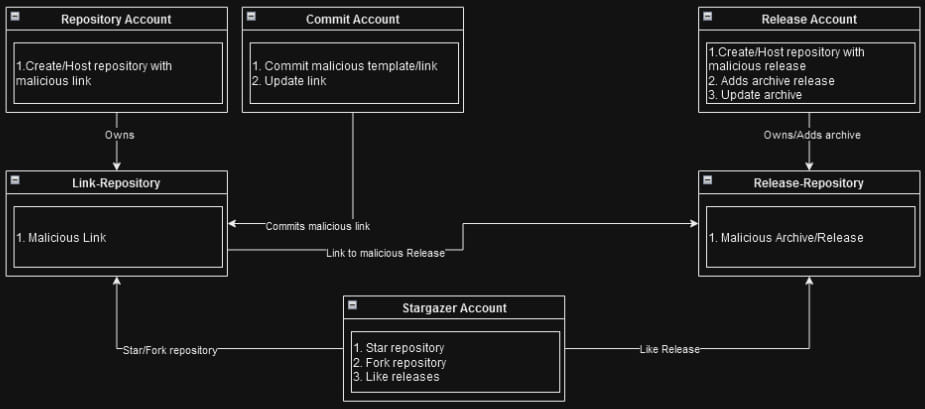
Stargazer Goblin has developed a system wherein they generate hundreds of repositories using 3.000 fake ‘ghost’ accounts. These accounts star, fork, and subscribe to malicious repositories to enhance their perceived legitimacy and boost their chances of appearing on GitHub’s trending section.
Ghost GitHub accounts participating in the scheme
Source: Check Point
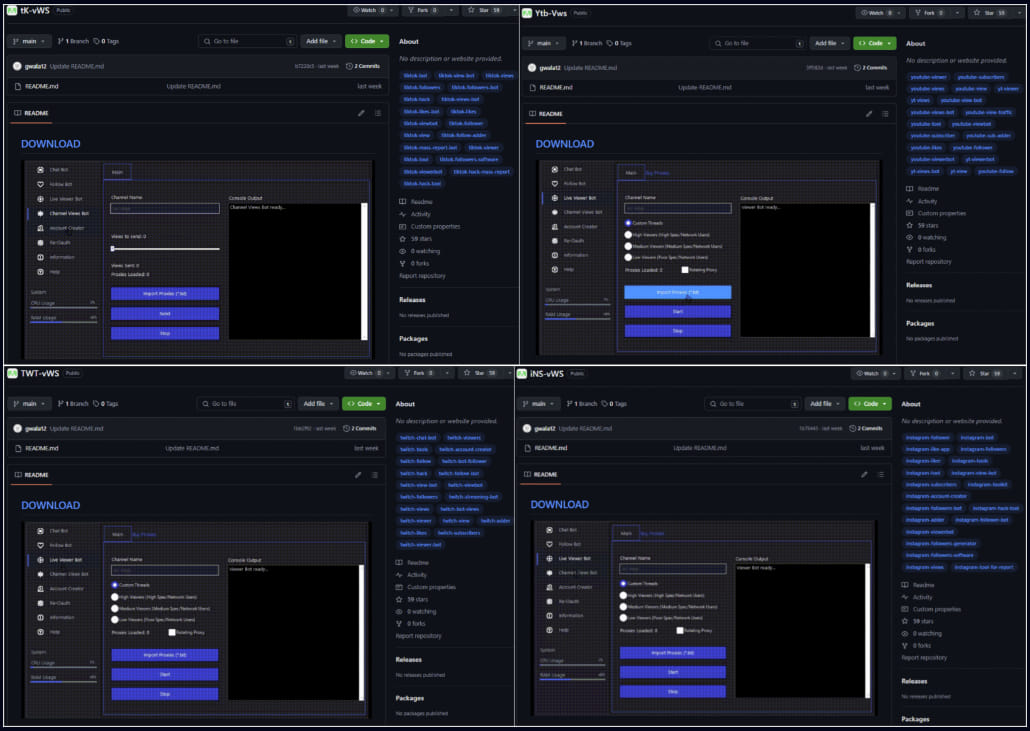
The repositories are labeled with project names and tags targeting specific interests such as
- cryptocurrency,
- gaming,
- and social media.
Phishing templates targeting different social media platform users
Source: Check Point
The ‘ghost’ accounts are assigned specific roles:
- one group handles the phishing template,
- another provides the phishing image,
- and a third delivers the malware,
thereby ensuring a level of operational resilience.
“The third account, which delivers the malware, is more prone to detection. When this occurs, GitHub bans the entire account, repository, and associated releases,” explains researcher Antonis Terefos.
In response, Stargazer Goblin updates the first account’s phishing repository with a new link to an active malicious release. This strategy allows the network to continue operating with minimal disruption when a malware-serving account is banned.”
Stargazers roles overview
Source: Check Point
Check Point has observed instances where a YouTube video with a software tutorial linked to one of the ‘Stargazers Ghost Network’ GitHub repositories.
The researchers suggest this could be one of multiple examples of channels used to direct traffic to phishing repositories or malware distribution sites.
Regarding the scale and profitability of the operation, Check Point estimates that the threat actor has earned over $100,000 since the service’s launch.
As for the types of malware distributed through the Stargazers Ghost Network, Check Point identifies
- RedLine,
- Lumma Stealer,
- Rhadamanthys,
- RisePro,
- and Atlantida Stealer,
among others.
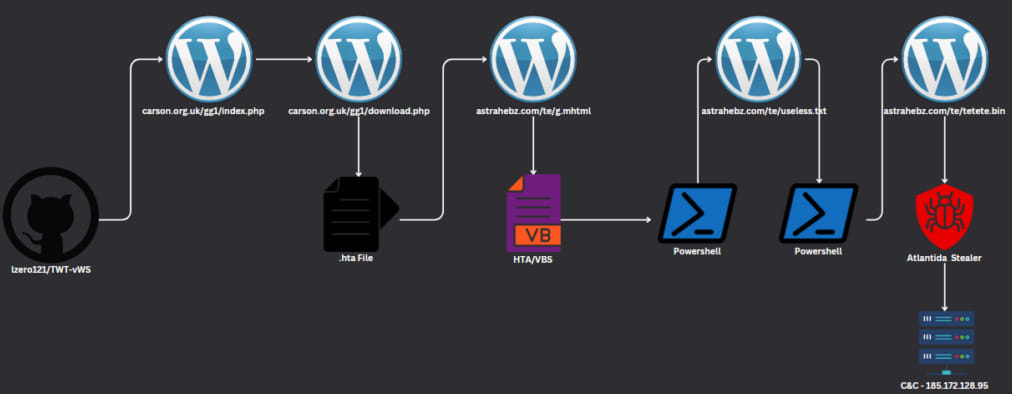
An example attack chain detailed in Check Point’s report
In an example attack chain detailed in Check Point’s report, the GitHub repository redirects visitors to a compromised WordPress site, where they download a ZIP archive containing an HTA file with VBScript.
Atlantida Stealer attack chain
Source: Check Point
The VBScript initiates the execution of two consecutive PowerShell scripts, ultimately leading to the deployment of Atlantida Stealer.
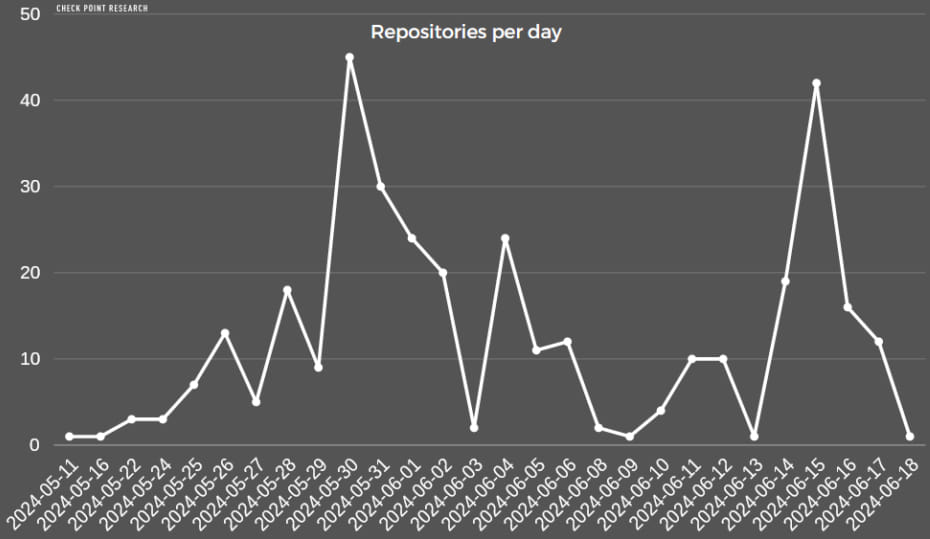
Although GitHub has removed over 1,500 malicious and fake repositories since May 2024, Check Point reports that:
- more than 200 remain active
- and continue to distribute malware.
Stargazer repositories added daily on GitHub
Source: Check Point
Users accessing GitHub repositories via
- malvertising,
- Google Search results,
- YouTube videos,
- Telegram,
- or social media
are advised to exercise extreme caution with file downloads and the URLs they click on.
This is particularly important for password-protected archives. They cannot be scanned by antivirus software. For such files, it is recommended to extract them on a virtual machine (VM). And scan the extracted contents with antivirus software to check for malware.
If a VM is not available, you can use VirusTotal. As it prompts for the password of a protected archive to scan its contents. However, VirusTotal can only scan a protected archive if it contains a single file.
Source: BleepingComputer, Bill Toulas
Read other news at our blog