The Internet Archive’s “Wayback Machine” has experienced a significant data breach following a cyberattack that compromised its website, exposing a user authentication database with 31 million unique records.
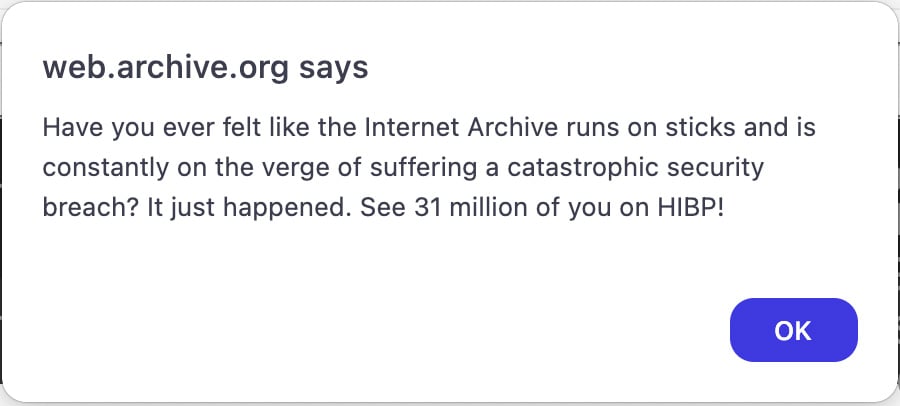
The breach came to light Wednesday afternoon when visitors to archive.org encountered a JavaScript alert created by the hacker, announcing the incident.
The alert read: “Have you ever felt like the Internet Archive runs on sticks and is constantly on the verge of suffering a catastrophic security breach? It just happened. See 31 million of you on HIBP!”
JavaScript alert shown on Archive.org
Source: BleepingComputer
“HIBP” refers to the Have I Been Pwned service, a data breach notification platform run by security expert Troy Hunt, where stolen data is often submitted.
According to Hunt, the hacker shared the Internet Archive’s authentication database nine days ago. The file, a 6.4GB SQL database labeled “ia_users.sql,” contains sensitive information for registered users, including email addresses, usernames, password change timestamps, Bcrypt-hashed passwords, and additional internal data.
The most recent timestamp on the stolen records is from September 28, 2024, which is likely when the breach occurred.
Hunt reported that the database contains 31 million unique email addresses, many of which are subscribed to the HIBP notification service. The data will soon be added to the platform, enabling users to check if their information was compromised in the breach.
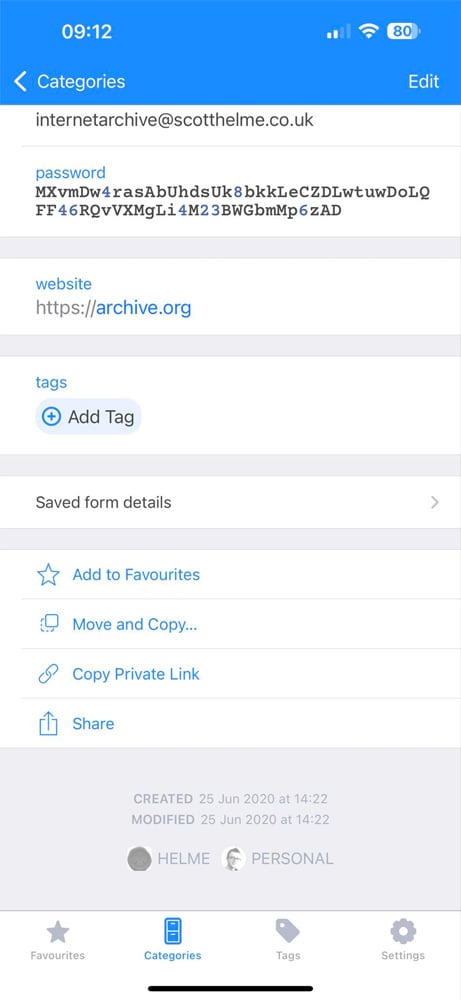
The breach’s authenticity was confirmed when Hunt reached out to individuals listed in the database, including cybersecurity expert Scott Helme, who allowed BleepingComputer to publish his exposed record.
9887370, [email protected],$2a$10$Bho2e2ptPnFRJyJKIn5BiehIDiEwhjfMZFVRM9fRCarKXkemA3PxuScottHelme,2020-06-25,2020-06-25,[email protected],2020-06-25 13:22:52.7608520,\N0\N\N@scotthelme\N\N\NHelme verified that the bcrypt-hashed password in the stolen data matched the bcrypt-hashed password stored in his password manager. Additionally, the timestamp in the database aligned with the date he last updated his password.
Password manager entry for archive.org
Source: Scott Helme
Hunt stated that he initiated a disclosure process with the Internet Archive three days ago, informing them that the data would be uploaded to the Have I Been Pwned service within 72 hours. However, he has not received any response since then.
At this time, it remains unclear how the threat actors gained access to the Internet Archive, or whether any additional data was compromised.
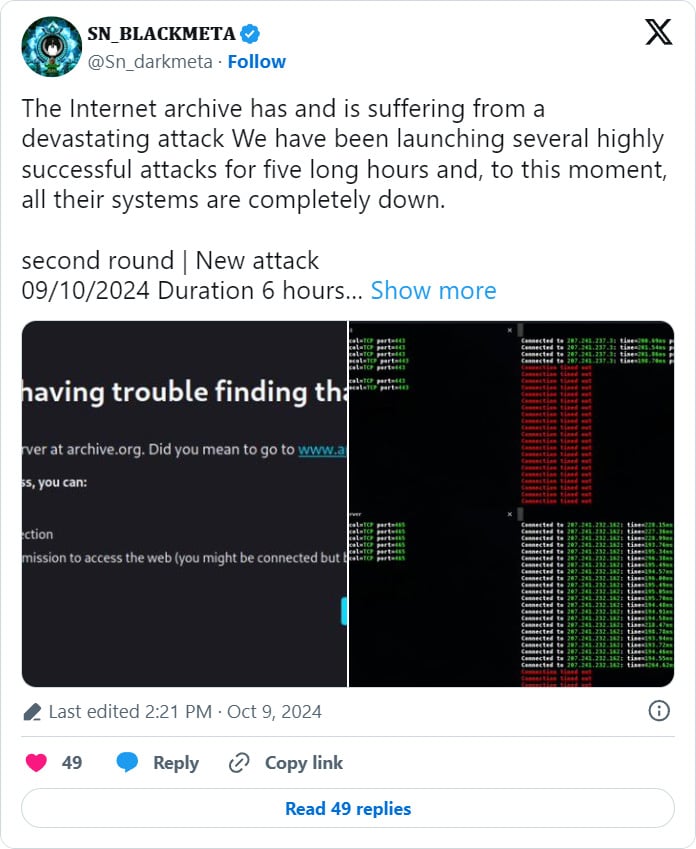
In a separate incident earlier today, the Internet Archive was targeted by a Distributed Denial-of-Service (DDoS) attack. The BlackMeta hacktivist group has claimed responsibility and announced plans for further attacks.
And yet there is no response from Internet Archive.
Source: BleepingComputer, Lawrence Abrams