IKEA, a Swedish furniture and homeware multinational, is facing a complex phishing campaign in progress, where cybercriminals are using internal company emails to send more fake messages to other employees. O BleepingComputer, who had access to internal company e-mails, reports that employees are being alerted of the attack.
The release details that cybercriminals are using IKEA’s internal emails to send false messages to other employees, partner organizations and even suppliers.
“There is a cyber attack going on that targets IKEA internal emails. Other organizations, suppliers and IKEA business partners are compromised by the same attack and are spreading malicious emails to people at IKEA. This means that the attack could come via email from someone you work with, from an outside organization, and in response to an existing conversation. So it’s hard to detect. We ask that you be extremely cautious. If you feel unsure, please email support with a copy of the suspicious email attached so we can act,” the statement writes.
To contain the case, IKEA said it has disabled the ability for employees to remove suspicious emails from quarantine. “Our email filters can identify some of the malicious emails and quarantine them. As the email can be a response to an ongoing conversation, it’s easy to think the email filter has made a mistake and release it from quarantine. Therefore, we are, until further notice, disabling the ability for everyone to release emails from quarantine“, writes the same statement.
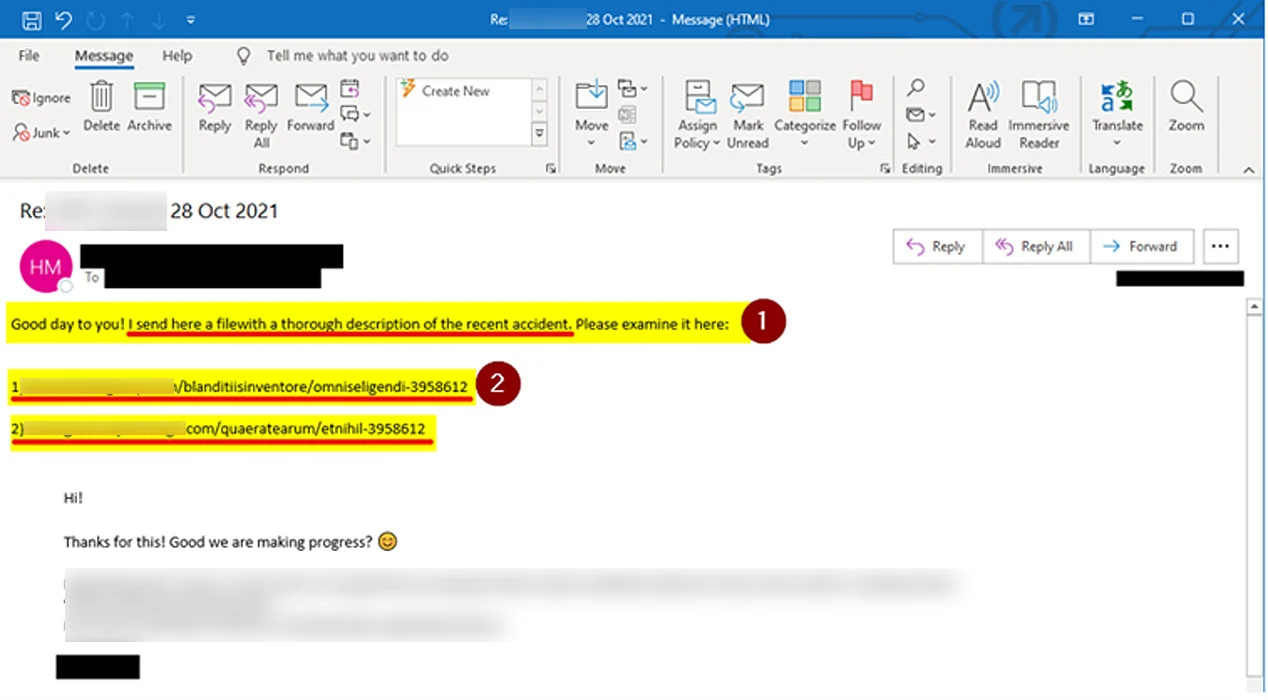
In this fake email sent to IKEA employees, cybercriminals have attached a malicious Excel spreadsheet, disguised as a legitimate spreadsheet, but installing malware on the victim’s machine. The attack directly affects the company’s email communication, which is an unstoppable tool. Because of this, IKEA is treating the case as a serious security incident, which can be escalated to an attack with even more serious damage.
Awareness
The writing of the the hack got in touch with Priscila Meyer, founder and CEO of Eskive, an information security platform, which provides and measures awareness programs, to understand how cybercriminals convince victims and do what they want and how companies can prevent their employees from being the victims.
According to Meyer, most security incidents (about 90%) are caused by the human factor directly or indirectly. “Phishing is one of the biggest corporate threats right now, especially when it comes to the risks associated with the human factor. There is no lack of data to say that the number of phishing cases increases every day“, explains.
This scenario was made even worse by the COVID-19 pandemic, which forced remote work, accelerating digital transformation with little planning and priority on security. “One of the causes of this increase in the number of phishing cases is that cybercriminals have realized that it is easier to attack the user than a computer system. The criminal will not try to circumvent the technology. The gateway is almost always the human factor.”
Although most companies are using automated spam and phishing detection technologies, we still can’t trust them. If we configure too many parameters, collaborators end up not receiving the emails they should and if we configure too few parameters, malicious emails pass through the filter.
“There are several options for technologies that can identify, based on criteria, whether that email is a phishing or not. The problem with these technologies is to restrict too much. If you restrict too much, we often have false positives and emails that were supposed to arrive do not arrive. Today the technology works very well, but we cannot trust it 100%, it will always send a malicious email”.
phishing anatomy
Meyer explains that it is common for cyber attacks to start with phishing campaigns, as it is easy and very effective for cybercriminals. As soon as victims fall for the scam, cybercriminals flock to technologies such as malware infection, trojans, or access credential collection, to move laterally in the victim’s system.
The critical point in these attacks is information.. If the cybercriminal has inside information, it’s easier to convince victims to do what he wants. Generic messages tend to be less effective than targeted campaigns. “There are several techniques of persuasion and social engineering that cybercriminals use to deceive their victims. It’s easier to convince someone when the attack is targeted, when you have inside information, which gives more credibility, what we call ‘spear phishing’, a more targeted phishing attack.”
Therefore, companies that seek to minimize the risks related to the human factor need their employees to be able to identify criminal campaigns on the internet. This is done with education and awareness, explains Meyer. “We first take information to people, so that they have adequate behavior and the wisdom to act when subjected to threats […] In addition to raising awareness, it is necessary to measure. It’s not just about passing on information. It is necessary to measure whether employee awareness is becoming a habit“.
Awareness programs start with an assessment to learn how mature a company is with respect to security awareness. After defining the scope and strategy, there is the delivery of information and training, going through tests and simulations, until reaching the report, which will indicate the weaknesses to be worked on. “The main objective of awareness-raising work is to minimize the risks of the human factor. We do this through education and awareness..”
Meyer believes that companies are no longer concerned about why to raise awareness among their employees, but how to do it. “Today companies have gone beyond ‘why raise awareness’ and are now asking themselves how to do it. They are really looking to improve their safety, training employees and investing in more appropriate behavior”, he concludes.
Source: TheHack