Cybercriminals linked to the Chinese state have been identified spying on the development of nuclear submarines from a company linked to the Russian army navy. The threat was identified by Cybereason’s cybersecurity research team Nocturnus.
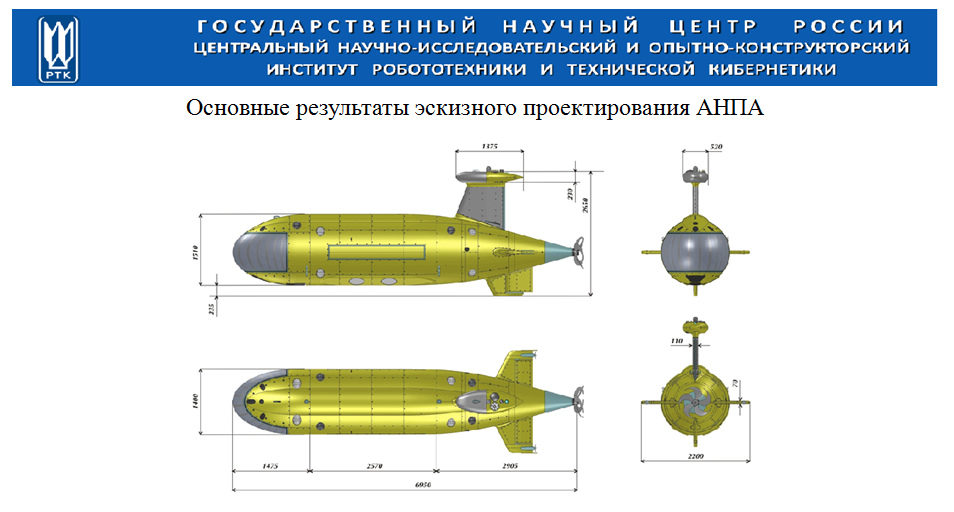
Russia’s nuclear submarines are being developed by the St. Petersburg Rubin Central Design Bureau of Marine Engineering (Rubin), one of the world’s leading submarine design centers, founded in 1901, as an arm of the state-owned United Shipbuilding Corporation (USC) Russian-made cargo and war ships.
According to Cybereason researchers Daniel Frank and Assaf Dahan, Chinese cybercriminals have organized a phishing campaign targeting Igor Vladimirovich, Rubin’s “respectable” CEO. Within the email, there was a malicious RTF file, created through Royal Road, a tool that generates malicious RTF files, very common among Chinese cybercriminals.
“RoyalRoad is used mainly by threat agents operating under the interests of the Chinese state (for example, Tick, Tonto Team, TA428, Goblin Panda, Rancor). [A Ferramenta] has very consistent characteristics and most weapon-turned RTF documents usually drop an encrypted file called “8.t”, what – once decrypted – can deliver a variety of payloads to different threat agents“, write the researchers in a report, published on Friday (04/30).
The researchers, who analyzed the malicious file (8.t), identified that the file exploits three vulnerabilities (CVE-2017-11882; CVE-2018-0798 and CVE-2018-0802) from Microsoft Equation Editor, to insert an undocumented backdoor, baptized by Cybereason as PortDoor.
Once configured on a victim’s network, PortDoor grants access to infected victim’s machines, collects information and deploys other malware and payloads, if necessary.
In addition, PortDoor is also able to steal and encrypt general data, identify which user is accessing infected machines, escalate privileges, manipulate configurations and processes.
“Portdoor has a number of features, including the ability to recognize, create target profiles, deliver additional loads, escalate privileges, process manipulation, static anti-virus evasion detection, one-byte XOR encryption, exfiltration of AES-encrypted data and more“, they write.
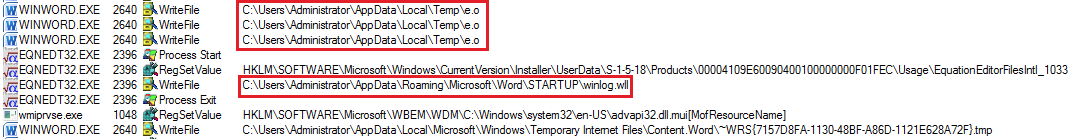
Although the Royal Road has already been widely used by Chinese state cybercriminals, the backdoor generated in this attack (PortDoor / 8.t) is a new variant, which is stored in the Microsoft Word startup folder, with the name “winlog.wll “.
“At the time of writing this report, it was not yet clear which actor of the threat is behind the new backdoor, however, we identified two possible suspects that fit the profile. There is currently not enough information available to prove the stated hypothesis with a high level of certainty “, conclude the researchers.
Source: Cybereason, TheHack.











