A newly discovered FileFix social engineering attack impersonates Meta account suspension warnings and tricks users into unknowingly installing the StealC infostealer malware.
FileFix represents a new variant of the ClickFix family of attacks. This family relies on social engineering techniques to lure users into pasting malicious commands into operating system dialog boxes as supposed “fixes” for problems.
Red team researcher mr.d0x created the FileFix technique, and instead of persuading users to paste malicious PowerShell commands into the Windows Run dialog or terminal, FileFix abuses the address bar in File Explorer to execute the commands.
Moreover, attackers have already weaponized FileFix in real-world campaigns. For instance, the Interlock ransomware gang used FileFix to install its remote access trojan (RAT). However, these earlier attacks relied on the original FileFix proof-of-concept (PoC) rather than adapting it with new lures.
The FileFix campaign
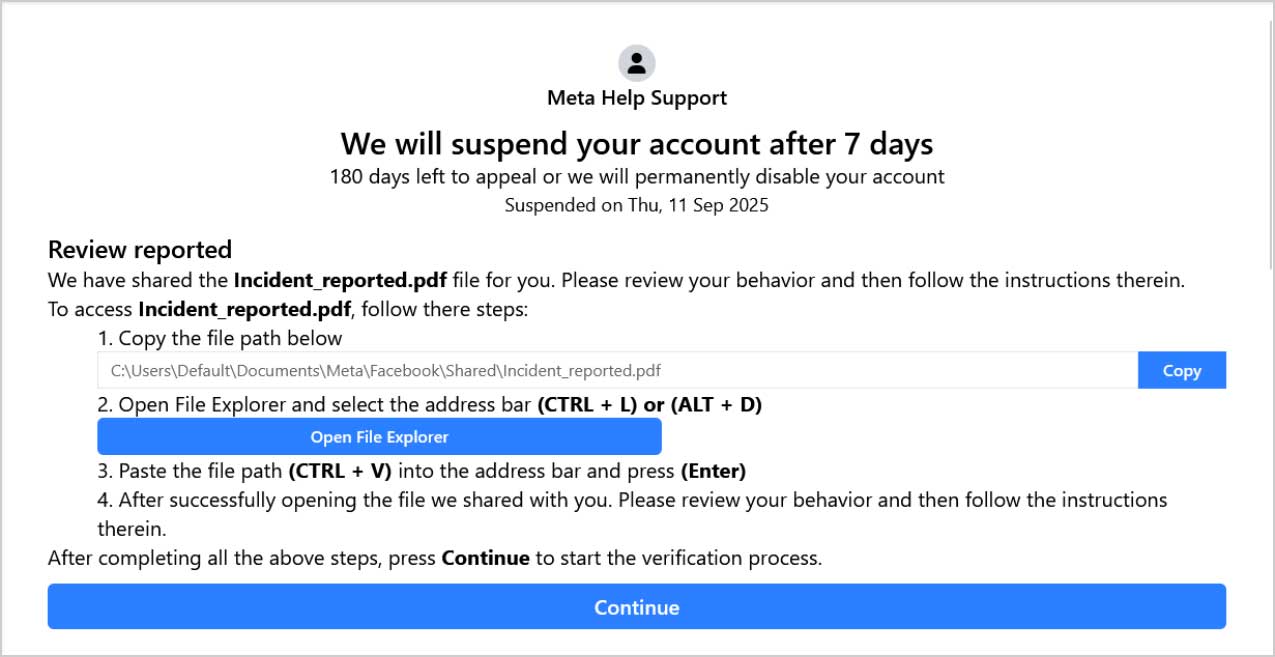
The new campaign, discovered by Acronis, deploys a multi-language phishing page that poses as Meta’s support team. It warns recipients that their account will be disabled in seven days unless they view an “incident report” allegedly shared by Meta.
However, the supposed report does not contain a document. Instead, attackers disguise a PowerShell command designed to install malware on victims’ devices.
The phishing page instructs users to click the “Copy” button to copy what looks like a file path, click the open File Explorer button, and then paste the path into the File Explorer address bar to open the document.
Yet, clicking the Copy button actually places a PowerShell command with added spaces into the Windows clipboard. As a result, only the file path appears when pasted into File Explorer.
“In order to trick the user into thinking that they are pasting the path to an ‘incident report’ PDF file, the attacker has placed a variable at the end of the payload, which contains a lot of spaces and the fake path at the end,” explains Acronis.
“This is done so that only the file path would appear in the address bar, and none of the actual malicious commands. In an average ClickFix attack, this is done using the # symbol instead of a variable, which is taken by PowerShell as a developer comment.”
“This has the unintentional advantage that anyone who has built their detections to look for the ‘#’ symbol from ClickFix, is likely to miss this.”
FileFix attack impersonating Meta support
Source: Acronis
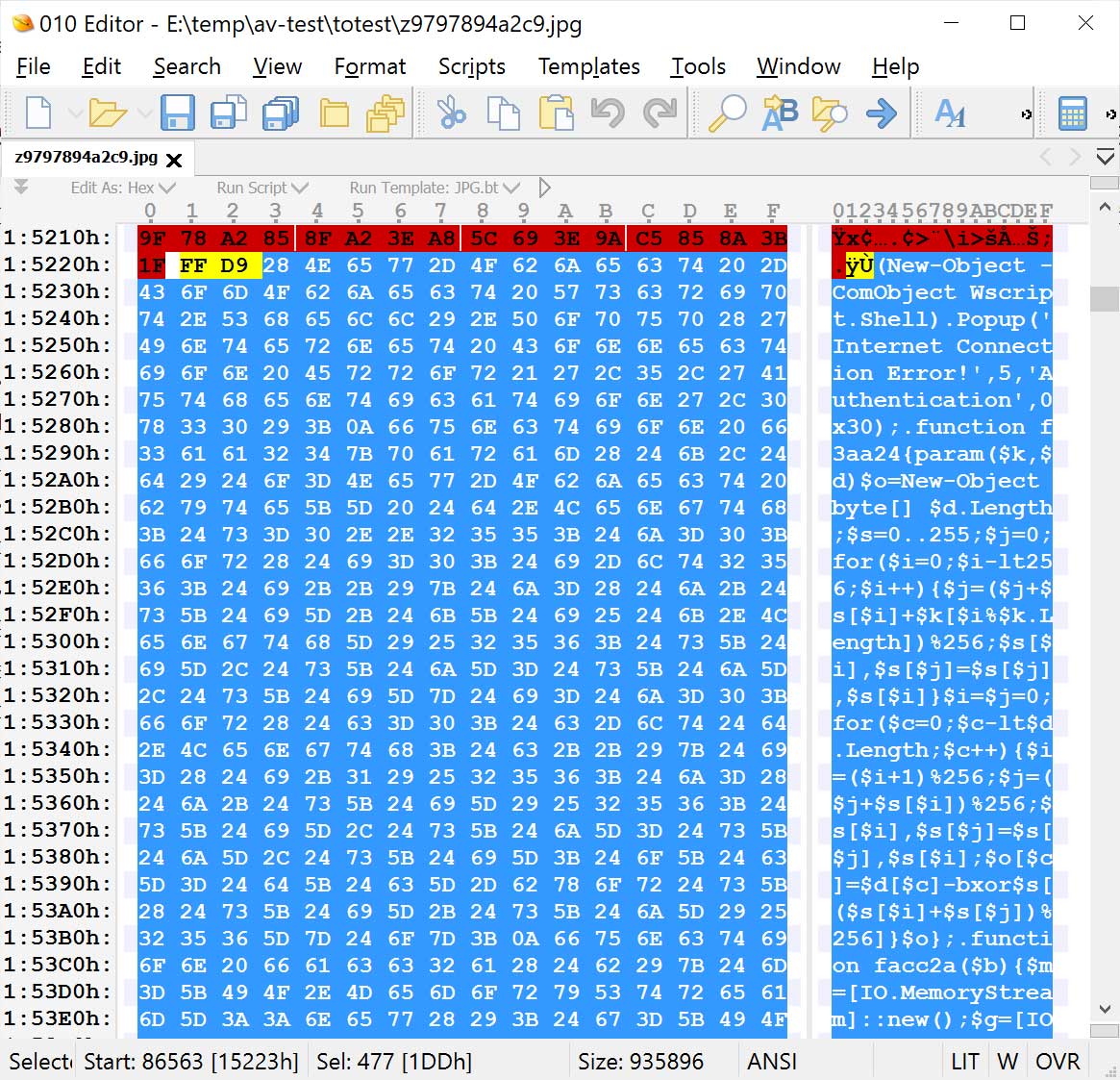
This FileFix campaign also stands out because it uses steganography to conceal both a second-stage PowerShell script and encrypted executables inside what appears to be a harmless JPG image hosted on Bitbucket.
The first-stage PowerShell command, unknowingly entered by the victim, downloads the image and extracts the embedded secondary script. That script then decrypts the payloads directly in memory.
Second PowerShell script embedded in image
Source: BleepingComputer
Ultimately, the attack delivers the StealC infostealer malware, which attempts to steal a wide range of data from infected devices, including:
- Credentials and authentication cookies from web browsers (Chrome, Firefox, Opera, Tencent, etc.)
- Credentials from messaging apps (Discord, Telegram, Tox, Pidgin)
- Cryptocurrency wallets (Bitcoin, Ethereum, Exodus, etc.)
- Cloud credentials (AWS, Azure)
- VPN and gaming apps (ProtonVPN, Battle.net, Ubisoft)
- Ability to capture a screenshot of the active desktop
Acronis observed multiple variants of this campaign over a two-week period, with attackers using different payloads, domains, and lures.
“Throughout our investigation, we’ve uncovered several iterations of the attack, going back two weeks,” observed Acronis.
“Through these iterations, we can trace out an evolution of both the social engineering technique, and the more technical aspects of the attack.”
“Perhaps this is indicative of an attacker testing out an infrastructure they are planning to use in the future, or perhaps these are iterations added to the attack mid campaign, as the attacker learns to adapt and improve.”
Although many organizations have already trained employees to recognize traditional phishing tactics, ClickFix and FileFix techniques remain relatively new and continue to evolve.
To address this, Acronis recommends that companies educate users on these emerging tactics and highlight the risks of copying data from a website into seemingly harmless system dialogs.
Source: BleepingComputer, Lawrence Abrams
Read more at Impreza News