A red-team tool known as EDRSilencer has been spotted in malicious activities, where it is being used to detect security tools and suppress their alerts to management consoles.
Cybersecurity researchers at Trend Micro have reported that attackers are increasingly incorporating EDRSilencer into their operations to avoid detection.
“Our internal telemetry revealed that threat actors are attempting to integrate EDRSilencer into their attacks, repurposing it as a method for bypassing security measures,” Trend Micro stated.
“Muting” EDR products
Endpoint Detection and Response (EDR) tools are security solutions designed to monitor and protect devices from cyber threats.
These tools leverage advanced analytics and regularly updated intelligence to detect both known and emerging threats, responding automatically while sending detailed reports to defenders about the threat’s origin, impact, and spread.
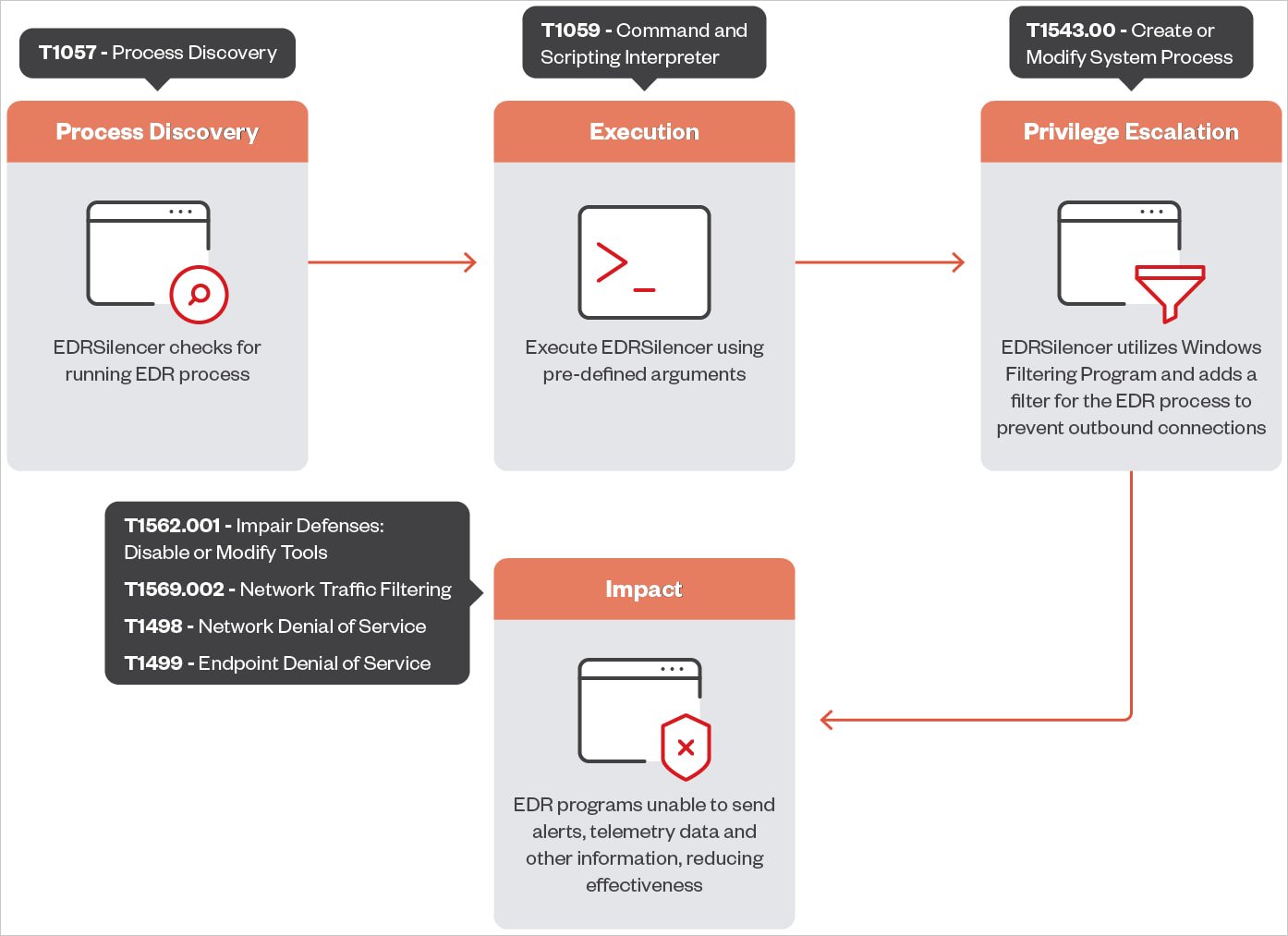
EDRSilencer is an open-source tool inspired by MdSec NightHawk FireBlock, a proprietary penetration testing tool. It detects active EDR processes and utilizes the Windows Filtering Platform (WFP) to monitor, block, or modify network traffic over IPv4 and IPv6 communication protocols.
WFP is commonly used in security products like firewalls and antivirus software, with its filters being persistent across the platform.
By setting custom rules, attackers can interrupt the constant data flow between an EDR tool and its management server, effectively preventing the delivery of alerts and detailed telemetry.
In its latest release, EDRSilencer can detect and block 16 modern EDR tools, including:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Secure Endpoint (formerly AMP)
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
Blocking the traffic of hardcoded executables
Source: Trend Micro
Tests by Trend Micro revealed that some EDR tools might still be able to transmit reports because certain executables are not included in EDRSilencer’s hardcoded list.
However, EDRSilencer allows attackers to add filters for specific processes by providing file paths, enabling them to extend the list of targeted processes and affect more security tools.
“After identifying and blocking additional processes not covered in the hardcoded list, the EDR tools failed to send logs, confirming the tool’s effectiveness,” Trend Micro noted in their report.
“This enables malware or other malicious activities to go undetected, heightening the risk of successful attacks without intervention,” the researchers added.
EDRSilencer attack chain
Source: Trend Micro
To combat EDRSilencer, Trend Micro suggests detecting the tool as malware and preventing it from disabling security measures.
Additionally, they recommend implementing multi-layered security controls to isolate critical systems, using security solutions with behavioral analysis and anomaly detection, monitoring for network compromise indicators, and applying the principle of least privilege to limit exposure.
Source: BleepingComputer, Bill Toulas














.jpg)