After discovering 28 malicious extensions to Google Chrome and Microsoft Edge last December, the Avast Threat Lab reveals that these extensions seek to steal sensitive information from Google accounts, hijack clicks and modify search results by sending victims to websites or fake advertisements. Among the findings of Avast experts is a new tactic to hide Command and Control (C&C) traffic, trying to make it look like Google Analytics traffic. Tactics to hide from malware developers and analysts have also been included.
According to Avast, the attacks took days and happened as follows:
- The victim downloads a malicious extension
- Three days after installation, the malicious code uses a secret channel to download an intermediate downloader
- The intermediate downloader downloads a CacheFlow payload;
- Each time the browser is run, the payload does the following:
- Performs developer and anti-analysis checks
- Make attempts to steal sensitive information from the user’s Google account
- Inject code into each new tab
- Steals user clicks and modifies your search results
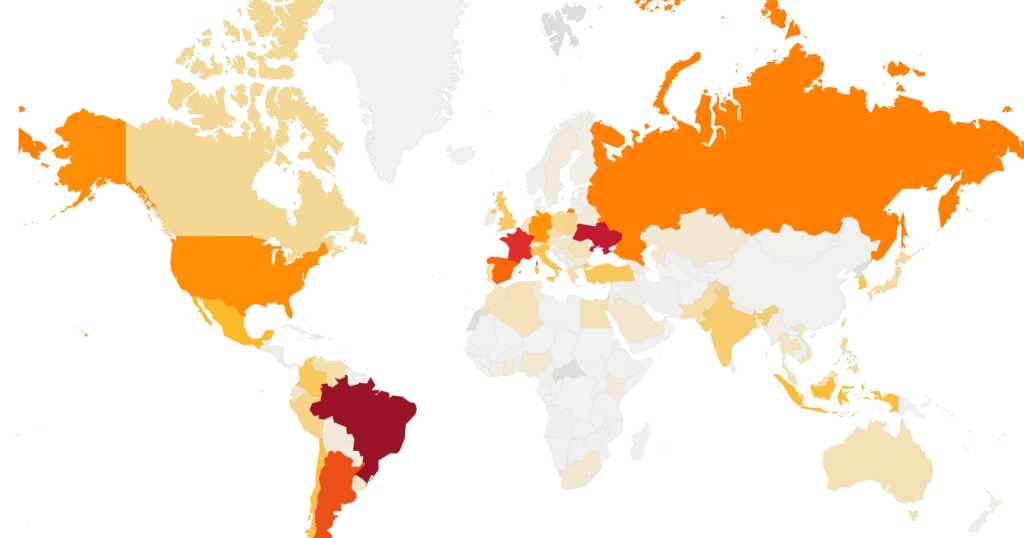
Avast points out that at least 3 million users worldwide have downloaded and installed the malicious extensions for Google Chrome. Based on its telemetry, the company also points out that the three main countries where users downloaded and installed CacheFlow extensions were: Brazil, Ukraine and France.
The Avast survey shows that extensions exhibited a fairly high level of stealth by employing many tricks to decrease the chances of detection. First, cybercriminals have avoided infecting users who are likely to be web developers. They determined this through extensions that the user installed or by verifying that the user accessed locally hosted websites. In addition, extensions delayed their malicious activity for at least three days after installation, to avoid an early warning. When the malware detected that the browser’s developer tools were open, it immediately disabled its malicious functionality. CacheFlow also scanned all Google search queries and if the user was searching for one of the malware’s Command and Control (C&C) domains, then he reported this to his C&C server and could also disable himself. According to user reviews on the Chrome Web Store, it appears that CacheFlow has been active at least since October 2017.
See the original post at: https://www.cisoadvisor.com.br/extensoes-do-chrome-e-edge-contaminaram-3-milhoes-de-usuarios/?rand=59039