A cybersecurity researcher is advising users to update Adobe Acrobat Reader immediately after a fix was released yesterday for a remote code execution zero-day (CVE-2024-41869) that has a public in-the-wild proof-of-concept exploit.
The flaw is a critical “use after free” vulnerability that could lead to remote code execution when opening a specially crafted PDF document.
A “use after free” bug occurs when a program attempts to access data from a memory location that has already been freed or released, leading to unexpected behavior like crashes or freezes.
If an attacker can inject malicious code into that freed memory, and the program subsequently accesses it, this could allow for malicious code execution on the targeted device.
This flaw has now been fixed in the latest versions of Acrobat Reader and Adobe Acrobat.
PoC exploit discovered in June
The Acrobat Reader zero-day was discovered in June through EXPMON, a sandbox-based platform developed by cybersecurity researcher Haifei Li to detect advanced exploits, including zero-days and hard-to-detect (unknown) exploits.
“I created EXPMON because I noticed there were no sandbox-based detection and analysis systems focused specifically on detecting threats from an exploit or vulnerability perspective,” Li explained to BleepingComputer.
“Most other systems focus on malware detection. The exploit/vulnerability perspective is crucial for more advanced or early detection.”
“For instance, if no malware is dropped or executed due to specific conditions, or if the attack doesn’t use malware at all, traditional systems would miss such threats. Exploits operate differently from malware, so a distinct approach is required to detect them.”
The zero-day was discovered after EXPMON analyzed a large number of samples submitted from a public source. Among them was a PDF containing a proof-of-concept exploit that triggered a crash.
Although the PoC exploit is still a work in progress and does not include a malicious payload, it was confirmed to exploit a “use after free” bug, which could be leveraged for remote code execution.
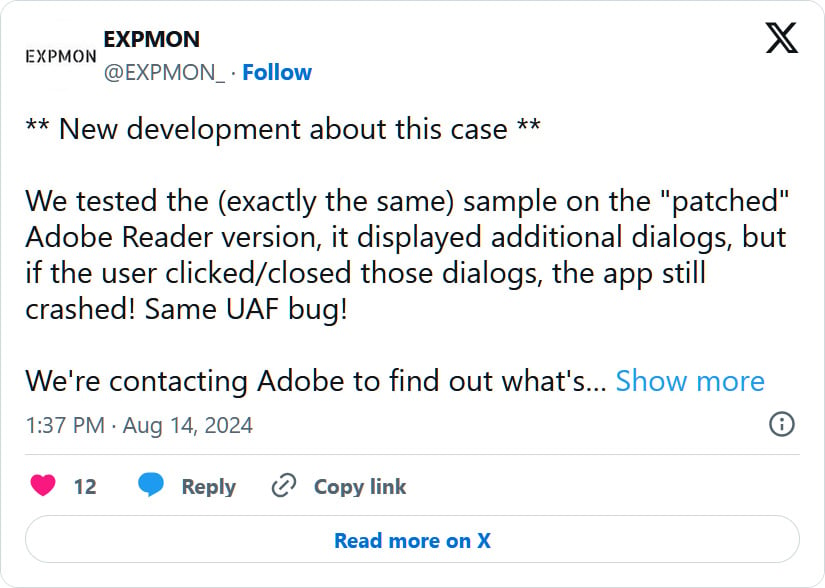
After Li disclosed the flaw to Adobe, a security update was released in August. However, the update did not fully resolve the issue, and the bug could still be triggered by closing certain dialogs.
“We tested the same sample on the ‘patched’ Adobe Reader version. It displayed additional dialogs, but if the user clicked or closed them, the app still crashed! Same UAF bug!” tweeted the EXPMON X account.
Yesterday, Adobe released a new security update that finally fixes the bug, now tracked as CVE-2024-41869.
Li plans to share details on how the bug was detected on EXPMON’s blog, with further technical information in an upcoming Check Point Research report.
Source: BleepingComputer, Lawrence Abrams