A DDoS mitigation service provider in Europe faced a massive distributed denial-of-service attack that reached 1.5 billion packets per second.
The attack came from thousands of IoT devices and MikroTik routers. However, FastNetMon, a company that provides protection against service disruptions, successfully stopped it.
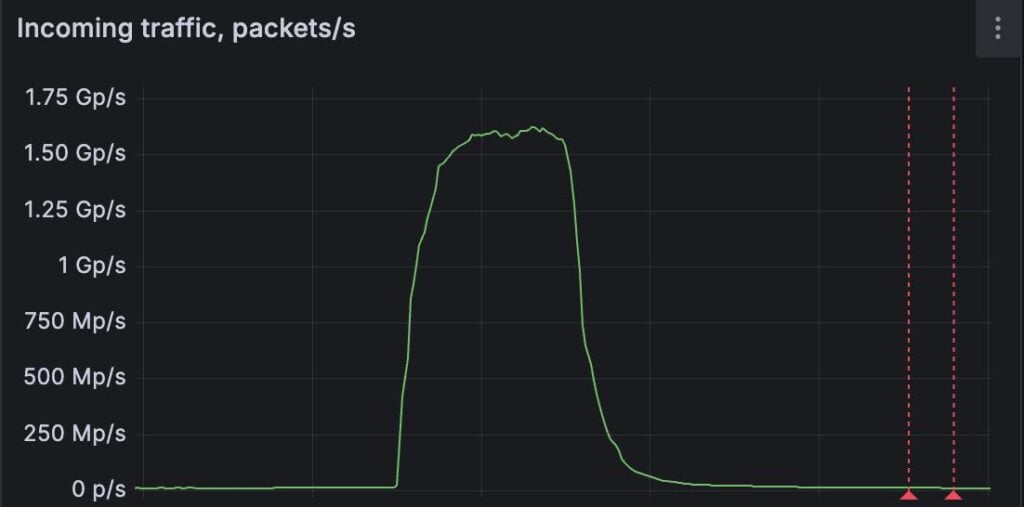
“The attack reached 1.5 billion packets per second (1.5 Gpps) — one of the largest packet-rate floods publicly disclosed,” FastNetMon says in a press release.
“The malicious traffic was primarily a UDP flood launched from compromised customer-premises equipment (CPE), including IoT devices and routers, across more than 11,000 unique networks worldwide,” the company explains.
The record-breaking DDoS attack
Source: FastNetMon
FastNetMon did not reveal the targeted customer. Instead, the company describes the victim as a DDoS scrubbing provider, a service that filters malicious traffic during DDoS attacks by using packet inspection, rate limiting, CAPTCHA, and anomaly detection.
The attack surfaced in real-time, and the customer’s DDoS scrubbing facility immediately initiated mitigation. The defense included deploying access control lists (ACLs) on edge routers known for amplification capabilities.
Meanwhile, news of this incident followed only days after internet infrastructure giant Cloudflare announced that it blocked the largest recorded volumetric DDoS attack in history, which peaked at 11.5 terabits per second (Tbps) and 5.1 billion packets per second (Bpps).
In both cases, the attackers aimed to overwhelm processing abilities on the receiving end and disrupt services.
FastNetMon’s founder, Pavel Odintsov, warned that the trend of massive attacks creates serious risks. He stressed that intervention at the internet service provider (ISP) level remains essential to stop the mass-scale weaponization of compromised consumer hardware.
“What makes this case remarkable is the sheer number of distributed sources and the abuse of everyday networking devices. Without proactive ISP-level filtering, compromised consumer hardware can be weaponised at a massive scale” – FastNetMon
“The industry must act to implement detection logic at the ISP level to stop outgoing attacks before they scale,” says Odintsov.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News