An information security researcher has identified a text injection vulnerability in XVIDEOS, one of the most popular pornographic content websites on the internet. The flaw was found in the .htaccess file, which is a required file for all websites using Apache servers. When exploited, it allows an attacker to direct the user to another page, it could be a fake page, a phishing page or even a page that offers malware and malicious code to the victim.
The vulnerability was reported to the company via the HackerOne bug bounty platform on August 19th and disclosed to the community on Sunday, September 19th. The Hack contacted the researcher, Muhammed Anzil (alone_breecher), to understand how the process was recognition, identification and follow-up of the correction with the company. Understand!
Anzil reveals that he found the vulnerability on the first day of analysis of XVIDEOS domains. The domain recognition and analysis process began shortly after XVIDEOS was launched at HackerOne on August 18th. “The next day I found the vulnerability,” he explains. As a reward, the researcher received U$100 from the company, which corrected the vulnerability immediately after its identification.
“While enumerating the XVIDEOS directories, I found a 403 error being reflected in the .htaccess file page, so I created some custom words to trick site users, saying that page was under construction, so they should visit another page, an attacker’s website”.
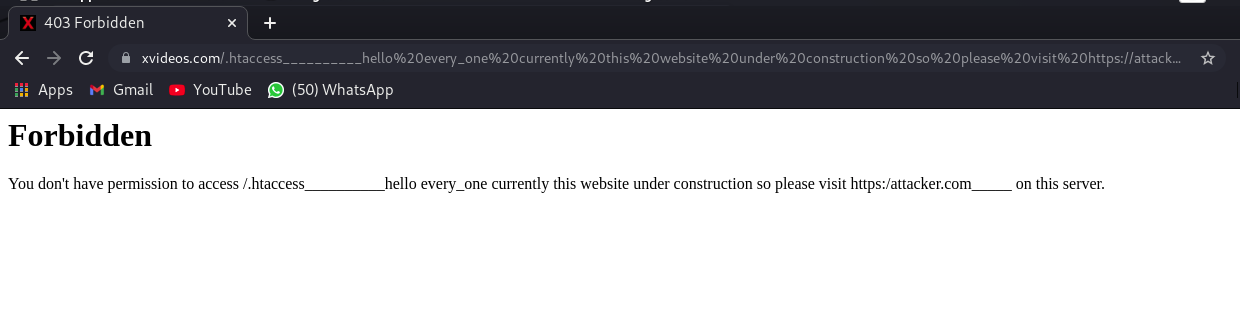
“After I found out XVIDEOS was on HackerOne, I wasted no time and started enumerating the site’s domains. I got my attention on the 403 status code on that page, which is like a banned page. I thought about the URL encoding and typed in some words that might change users’ minds, to something like: This site has been moved to: [malicious link]”, he explains.
Anzil explains that a cybercriminal can tamper with the URL of a legitimate domain, in this case xvideos[.]com to send users to fake pages outside the XVIDEOS domain, even if the attack started from a page with a legitimate address.
“The address is xvideos[.]com, so users think this is a verified porn site, but when the user clicks on the page he gets this message as if the site is down and is prompted to click on a supposed alternative, but that, in the case of an attack, it is the domain of an attacker”, explains Anzil about the possibilities of exploiting the flaw in a real situation.
The researcher regrets that in some cases, this vulnerability is not interpreted as something dangerous and it is common not to receive rewards for it. “This attack is widely misinterpreted as one that does not negatively impact […] I didn’t expect to receive a reward for this“, account. “Thanks to bug bounty my life is moving”, concludes the researcher.
Source: TheHack











