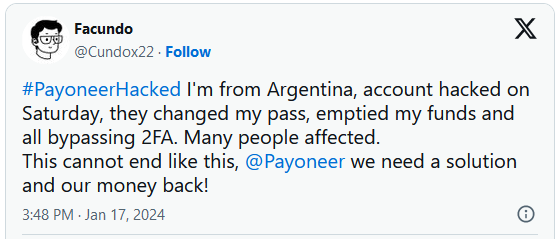
Numerous Payoneer users in Argentina report waking up to find that their 2FA-protected accounts were hacked and funds stolen after receiving SMS OTP codes while they were sleeping.
Payoneer is a financial services platform providing online money transfer and digital payment services. It is popular in Argentina because it allows people to earn in foreign currencies while bypassing local banking regulations.
Starting last weekend, many Payoneer users in Argentina, whose accounts were protected by two-factor authentication (2FA), reported suddenly losing access to their accounts or simply logging in to empty wallets, losing “years of work” worth in money ranging from $5,000 to $60,000.
The users report that right before this happened, they received an SMS requesting approval from a password reset on Payoneer, which they didn’t grant. Many say they didn’t click on the URLs, and some claim not even seeing the SMS until after the heist had been completed.
Many impacted said their stolen funds were sent to an unknown email address at the 163.com domain.
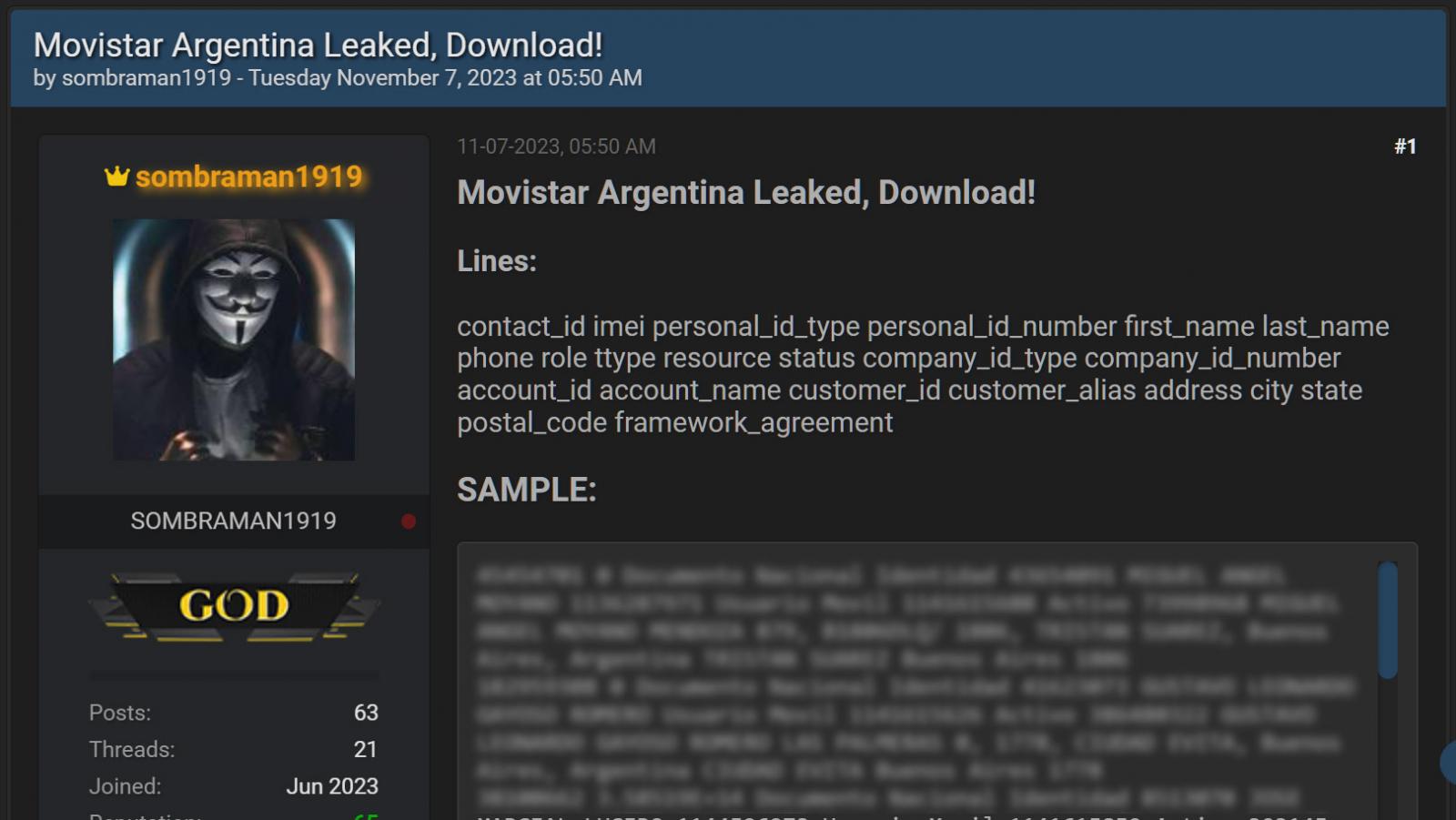
Local journalists have been interviewing victims and tracking the hacks and discovered that most affected users were customers of the mobile service providers Movistar and Tuenti, with the majority using Movistar.
This has raised suspicions that a recent Movistar data leak may be behind the account hacks, but the data leak did not expose users’ email addresses, which are required to reset passwords on Payoneer accounts.
Stolen Movistar data for Argentinians leaked on a hacking forum (Source: BleepingComputer)
Another theory is that the SMS provider used to deliver OTP codes was breached, allowing the threat actors to access codes sent by Payoneer.
Unfortunately, an official statement from Movistar shared by journalist Julio Ernesto Lopez does not address this theory, simply stating that the telecom provider is not responsible for messages sent through its network. However, Movistar said they have taken action to block the numbers used in the smishing campaign.
Update Payoneerhacked@MovistarArg aclara que ellos solo reciben el mensaje y no tienen responsabilidad.
Concuerdo. El problema está en el gateway usado por @Payoneer en la última milla para llega a Movistar https://t.co/56SLbrTrII pic.twitter.com/ZlmewSEbrl— Julio Ernesto Lopez (@julitolopez) January 18, 2024
“We inform you that Movistar is not responsible for the messages (or their content) that third parties send using its network,” reads the statement. (machine translated)
“Notwithstanding the above, we have taken preventive measures with those numbers from which some customers have reported receiving such communications.”
Payoneer has not provided specific answers about the attack yet but acknowledged the issue and mentioned it is working with authorities to address the fraud, which it believes is the result of phishing.
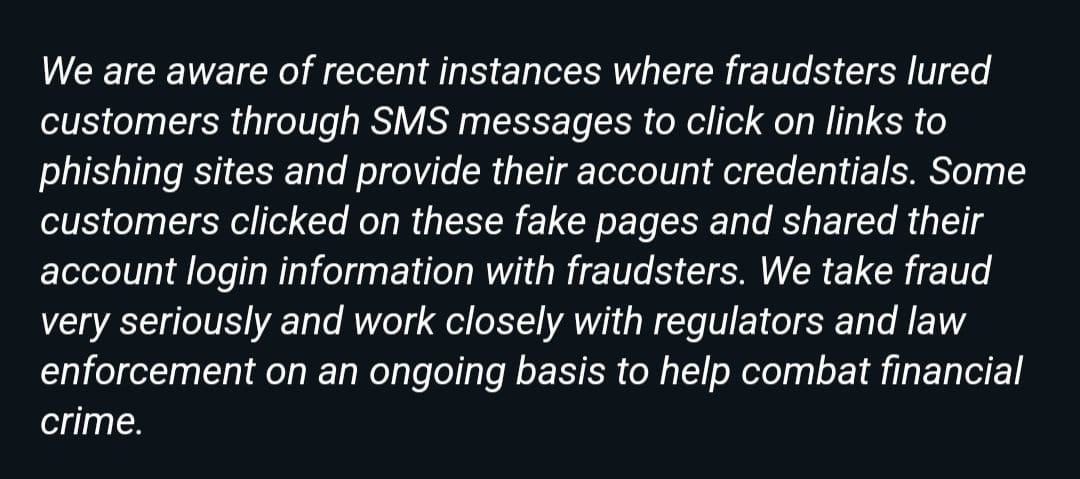
Tech reporter Juan Brodersen received a statement from Payoneer that puts the blame on the users, alleging that they clicked on the URLs in the SMS phishing texts and then entered their login details on phishing pages.
Payoneer statement (Source: @juanbrodersen)
However, many affected by the account hacks state that they did not click on phishing links, accusing Payoneer of attempting to deflect responsibility and failing to acknowledge a potential error or vulnerability within the platform.
Furthermore, Lopez told BleepingComputer that Payoneer requires a new SMS OTP code to be entered when you add a new destination address and then again when you wire money. If this was a phishing attack stealing OTP codes for the password reset, the threat actors should not have had access to later OTP codes required for these transactions.
While the hacks may be allowed by a 2FA bypass bug, like we saw last year with Comcast, other countries would likely be affected by the attacks.
Due to this, the attack’s precise mechanism remains unclear, with various hypotheses at play. A significant weakness in Payoneer’s system is its reliance on SMS-based 2FA, further compounded by the platform’s password recovery process, which only requires an SMS code.
BleepingComputer has contacted Payoneer with a request for a comment on the above, the status of their investigation, and whether they plan to offer restitution in the case that a weakness in its system is discovered to be the source of the hacks, but we have not heard back yet.
Until the situation clears up on who’s to blame and what exactly happened, Payoneer users in Argentina are advised to withdraw funds from their accounts or disable SMS-based 2FA and reset their account password.
Update 1/20 – A Payoneer spokesperson has sent BleepingComputer the following comment:
We are aware of recent instances where fraudsters lured a very limited number of customers to click on links to phishing sites and provide their account credentials.
Unfortunately, some customers clicked on these fake links and shared their account login information with fraudsters or encountered newer modes of fraud that compromised their mobile phones.
We took swift action to contain the attempts at fraud from spreading. We take fraud prevention very seriously and we work closely with regulators, mobile carriers, and law enforcement agencies on an ongoing basis to help combat financial crime.
We also continue to actively educate our customers on how to keep their accounts safe and protect their confidential information.
Regarding restitution, every case is different so while we can’t confirm funds can be recovered in each instance, we are working around the clock to protect customers’ funds and recover anything possible.
Source: BleepingComputer, Bill Toulas