Researchers have found over 20,000 instances of publicly exposed data center infrastructure management (DCIM) software that monitor devices, HVAC control systems, and power distribution units, which could be used for a range of catastrophic attacks.
Data centers house costly systems that support business storage solutions, operational systems, website hosting, data processing, and more.
The buildings that host data centers must comply with strict safety regulations concerning fire protection, airflow, electric power, and physical security.
Years of pursuing operational efficiency have introduced “lights-out” data centers, which are fully automated facilities managed remotely and generally operate without staff.
However, the configuration of these systems isn’t always correct. As a result, while the servers themselves may be adequately protected from physical access, the systems that ensure physical protection and optimal performance sometimes aren’t.
Multiple cases of unprotected systems
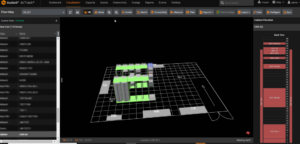
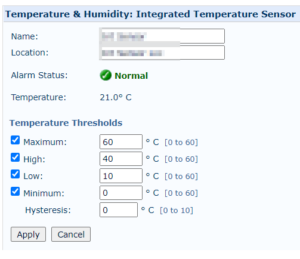
Investigators at Cyble have found over 20,000 instances of publicly exposed DCIM systems, including thermal and cooling management dashboards, humidity controllers, UPS controllers, rack monitors, and transfer switches.
Rack details on the exposed data center
Source: Cyble
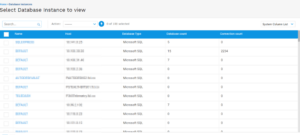
Additionally, the analysts were able to extract passwords from dashboards which they then used to access actual database instances stored on the data center.
Databases accessed in second phase
Source: Cyble
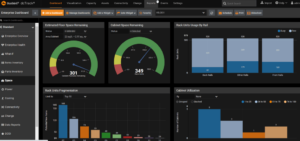
The applications found by Cyble give full remote access to data center assets, provide status reports, and offer users the capacity to configure various system parameters.
Sunbird dashboard
Source: Cyble
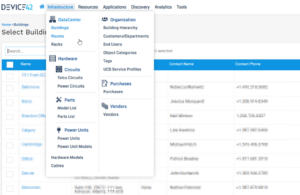
In most cases, the applications used default passwords or were severely outdated, allowing threat actors to compromise them or override security layers fairly easily.
Device42 systems dashboard
Source: Cyble
Potential impact
Exposing these systems without adequate protection means that anyone could change the temperature and humidity thresholds, configure voltage parameters to dangerous levels, deactivate cooling units, turn consoles off, put UPS devices to sleep, create false alarms, or change backup time intervals.