According to researchers at the PrivacySharks website, GIGABYTE — a Taiwanese giant that produces motherboards, video cards, computers and peripherals in partnership with several other companies in the field — was the victim of yet another ransomware attack. This time, the AvosLocker gang kidnapped and stole the brand’s sensitive files, which posted a statement on its deep web site claiming to be in possession of several highly sensitive documents from the Asian manufacturer.
Although GIGABYTE still has time to make a possible negotiation with the kidnappers, the AvosLocker syndicate, as usual in its modus operandi, is already offering the stolen material for sale. PrivacySharks took a 14.9 MB sample of the collection and found that most of the information concerns data from employees and employees of the Nova Taipei company. In addition, confidentiality terms were also found with the American Barracuda Networks.
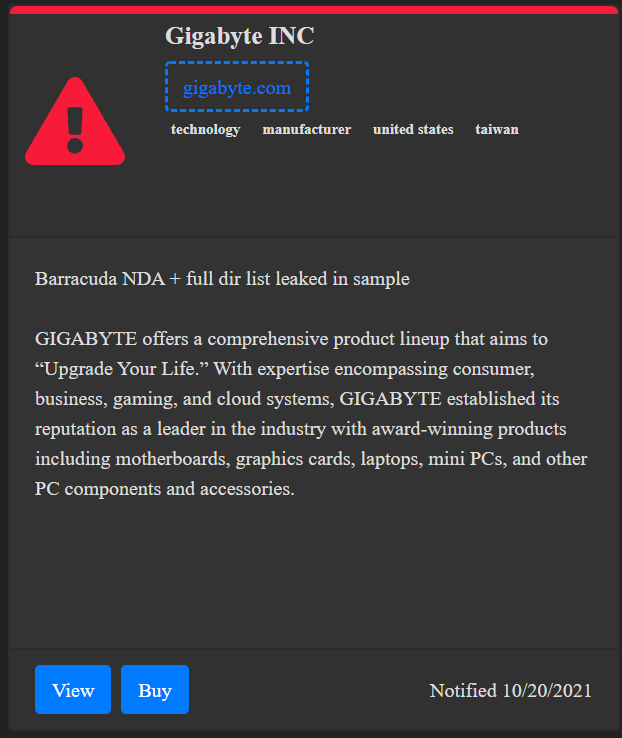
“Data leakage has the potential to damage GIGABYTE’s relationships with third-party companies, as its agreement with Barracuda Networks and signed between the two companies has been exposed. Revealing Financial Arrangements Could Damage GIGABYTE’s Bargaining Power In Future Negotiations or make companies afraid to go into business with the technology company for fear that the data will be exposed,” explains Madeleine Hodson of PrivacySharks.
As for the other information exposed, the amount of details about its employees and old selection processes that the Taiwanese kept is worrying: employee credentials, payrolls, resumes, passports, images of private events in the brand’s offices, invoices for various expenses on business trips and data from more than 1.5 thousand candidates. Old credit card numbers were also found. and that they are possibly expired.
The candidates’ part is particularly serious, since demonstrates irresponsibility on the part of the company when storing information that is no longer useful to it. “As a general rule, companies should not retain candidate data after the hiring process is complete, and GIGABYTE’s data leakage demonstrates why, as this information can fall into the wrong hands. For this reason, the European Union has the GDPR law that requires companies to delete data like these”, adds Madeleine.
Another supply chain attack?
Believe it or not: the worst is yet to come. PrivacySharks experts found two .KEY files and some .CRT files — if criminals managed to get hold of GIGABYTE’s master keys (used to identify the company’s software as legitimate), they could force any branded hardware to update its firmware, driver, or BIOS to a malicious edit corrupted by miscreants, in a supply chain maneuver à la SolarWinds.
It is noteworthy that this this is the second time in 2021 that GIGABYTE has suffered a ransomware attack. As we reported here at The Hack, the company also had a total of 112GB of data hijacked by the RansomEXX gang.
Sources: PrivacySharks, TheHack.