Cybercriminals, possibly linked to the government of China, are targeting attacks on telecommunications and mobile internet companies to spy on 5G development secrets. The campaign was identified by McAfee as part of Operation Diànxùn.
McAfee researchers believe that professionals from technology, communication and internet companies are targeted by a group of Chinese cyber spies, which uses tactics, techniques and procedures (TTPs) very similar to that of a Chinese group known as RedDelta, or Mustang Panda.
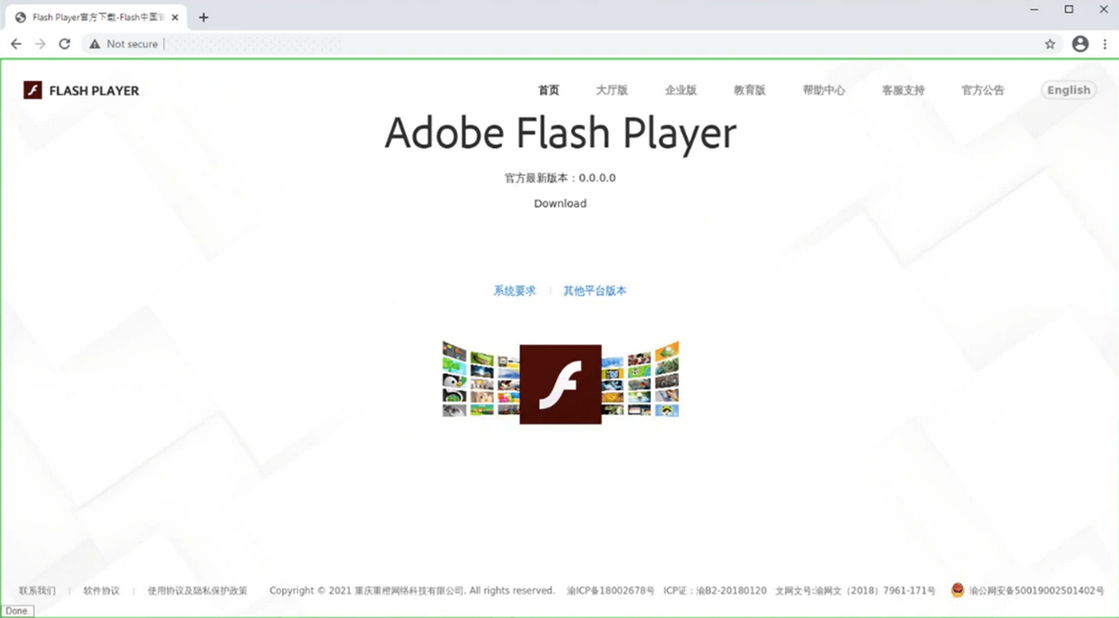
They explain what the group’s objective would be get confidential data and information from companies working on the development and application of 5G, Through a Huawei’s fake domain, which infects victims with malware disguised as a Flash installer.
“We discovered malware that disguised itself as a Flash application, usually connecting to domains” update[.]careerhuawei[.]net ”and” update[.]huaweiyuncdn[.]com “who were under the control of the threat actor. The malicious domain was created to look like Huawei’s legitimate career site, which has the domain “career[.]huawei[.]with “.”, explain the researchers.
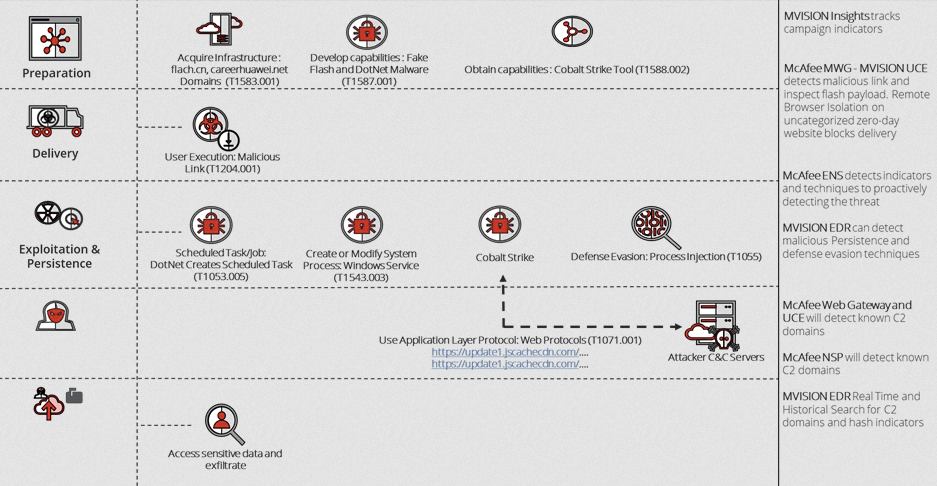
Cybercriminals even registered the domain “flach.cn” for deceive victims into believing that the website (which offers malware in disguise) is a legitimate domain of the technology Flash, in China, but that runs malware, like a DotNet payload and in the future, backdoors, on the victim’s machine.
“The DotNet payload contains several functions and acts as a utility to further compromise the machine [da vítima], a tool to manage and download backdoors on the machine and configure its persistence“, explains the regional solutions architect, Andrea Rossini.
Lastly, a backdoor is set up that allows remote access, through a command and control server, plus a Cobalt Strike beacon.
According to the Threat Post, one of the groups with very similar tactics and procedures, RedDelta, which also operated under the name Mustang Panda and is linked to the Chinese state, is suspected of organizing attacks against the Catholic Church, last year, as it has also performed attacks against NGOs and used malware commonly associated with other groups in the Chinese state, like Poison Ivy and PlugX.
See the original post at: https://thehack.com.br/cibercriminosos-ligados-ao-governo-da-china-direcionam-ataques-as-empresas-de-telecom-em-busca-de-segredos-do-5g/?rand=48873











