Salesforce Ransom
Salesforce has confirmed that it will not negotiate with or pay a ransom to the threat actors behind a massive wave of data theft attacks that impacted the company’s customers this year.
As first reported by Bloomberg, Salesforce emailed customers on Tuesday to explain that they would not pay a ransom. The company also warned that “credible threat intelligence” indicates the threat actors plan to leak the stolen data.
“I can confirm Salesforce will not engage, negotiate with, or pay any extortion demand,” Salesforce also confirmed to BleepingComputer.
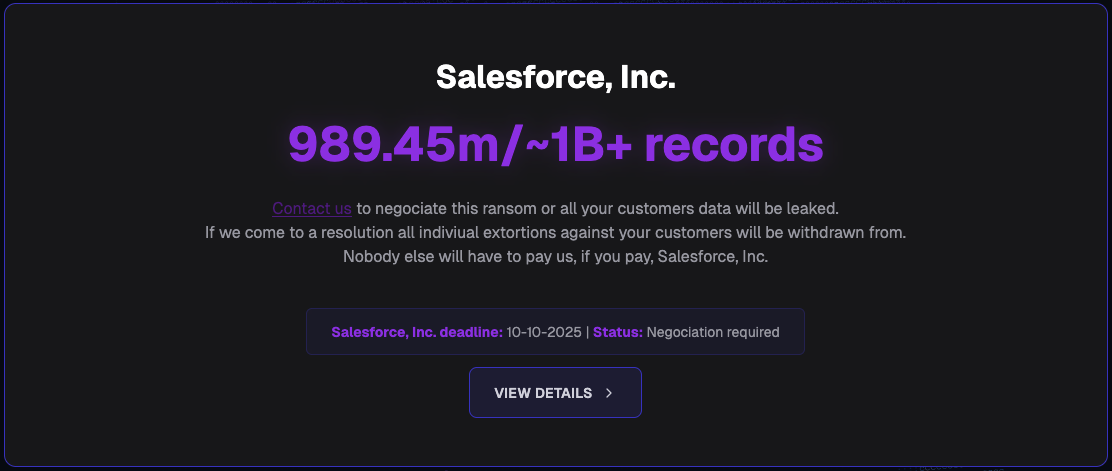
This statement follows the launch of a data leak site by the threat actors known as “Scattered Lapsus$ Hunters.” These attackers are attempting to extort 39 companies whose data they stole from Salesforce. They hosted the website on the breachforums[.]hn domain, which takes its name from the notorious BreachForums website—a hacking forum infamous for selling and leaking stolen data.
The extortion site lists several well-known brands and organizations, including FedEx, Disney/Hulu, Home Depot, Marriott, Google, Cisco, Toyota, Gap, Kering, McDonald’s, Walgreens, Instacart, Cartier, Adidas, Saks Fifth Avenue, Air France & KLM, Transunion, HBO MAX, UPS, Chanel, and IKEA.
In total, the threat actors claim to have stolen nearly 1 billion data records. They threaten to release the data publicly unless the individual companies—or Salesforce itself—pay the extortion demand, either separately or as a single payment covering all affected customers listed on the site.
ShinyHunters Salesforce data leak site
Source: BleepingComputer
Salesforce confirmed that attackers stole the data from its instances during two separate campaigns that took place in 2025.
The Data Breach
The first data theft campaign began at the end of 2024. During this attack, the threat actors used social engineering tactics by impersonating IT support staff to trick employees into connecting a malicious OAuth application to their company’s Salesforce instance.
After establishing this connection, the attackers downloaded and stole company databases, then used them for extortion through email.
These social engineering attacks affected companies such as Google, Cisco, Qantas, Adidas, Allianz Life, Farmers Insurance, Workday, Kering, and several LVMH subsidiaries, including Dior, Louis Vuitton, and Tiffany & Co.
The second Salesforce data theft campaign started in early August 2025. This time, the threat actors used stolen SalesLoft Drift OAuth tokens to pivot into customers’ CRM environments and exfiltrate sensitive data.
The SalesLoft data theft attacks mainly targeted support ticket data, which the attackers scanned for credentials, API tokens, authentication tokens, and other sensitive information. With these details, they could breach company infrastructure and cloud services.
One of the attackers behind the SalesLoft campaign, known as ShinyHunters, told BleepingComputer that they stole approximately 1.5 billion data records belonging to over 760 companies.
Many organizations have already confirmed that these SalesLoft supply-chain attacks affected them, including Google, Cloudflare, Zscaler, Tenable, CyberArk, Elastic, BeyondTrust, Proofpoint, JFrog, Nutanix, Qualys, Rubrik, Cato Networks, Palo Alto Networks, and others.
The Data
The recently launched data leak site primarily targeted customers affected by the original social engineering attacks. The threat actors announced that they would begin publicly extorting victims of the SalesLoft attacks after October 10th.
However, the data leak site has since shut down. Its domain now uses the nameservers surina.ns.cloudflare.com and hans.ns.cloudflare.com—both of which the FBI has previously used when seizing domains.
BleepingComputer contacted the FBI to verify whether they seized the domain but has not received a response at this time.
Source: BleepingComputer, Lawrence Abrams
Read more at Impreza News