Update 19/04/2021 10h30: after Fiocruz’s official positioning, saying that the vulnerabilities were found on a test server, the researcher sent us images indicating that the accessed server is located in Rio de Janeiro and in Manguinhos, cities where they are concentrated vaccine production. See the images in the subtitle “Official positioning“.
A security researcher independent, who preferred to be identified as “Hacker of Good”, found vulnerabilities in a vaccine control and storage system from the Oswaldo Cruz Foundation (Fiocruz), a carioca institution that is producing vaccines against COVID-19 with inputs from Oxford / AstraZeneca.
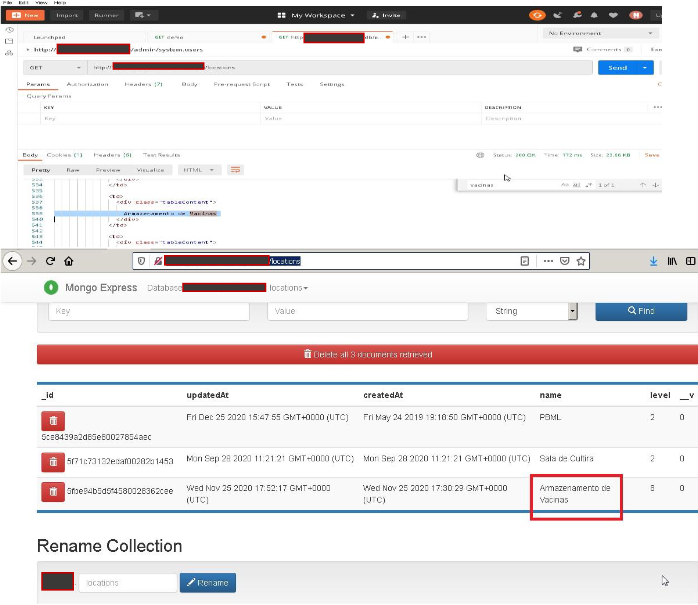
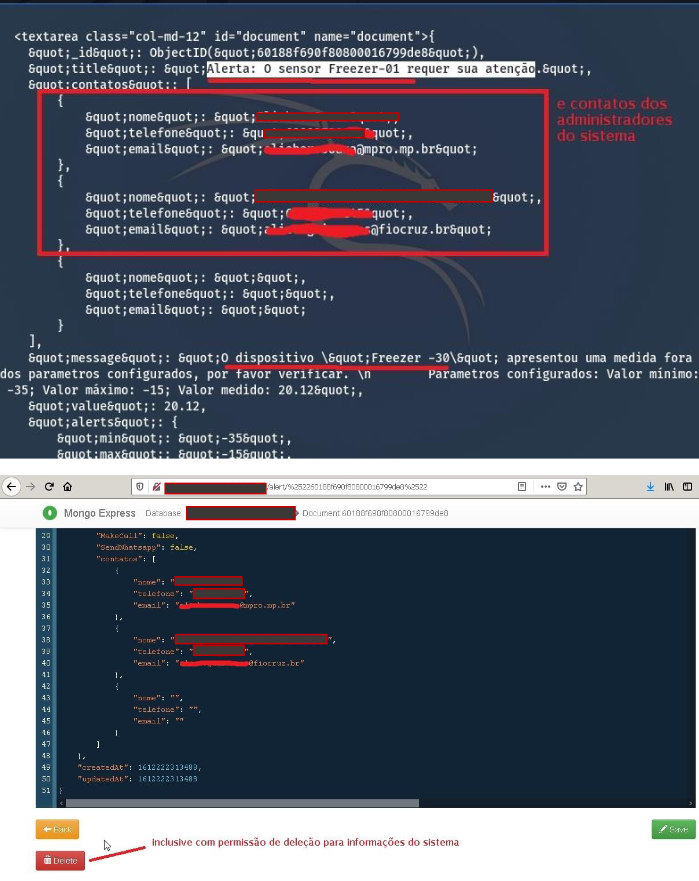
Through a report sent to Fiocruz, which The Hack had access to, the researcher explains that gained access to a database with information on vaccine management (greenhouses and freezers), research and data and employee credentials. With access to the system, it was it is possible to turn off freezers and change controls, reveal data such as employee email, password and phone number.
“Even with a security and firewall mechanism it was possible to map the services with firewall bypass techniques [e com isso] view internal information, such as freezers that cool vaccines and perform measurements, information from greenhouses and freezers, with the possibility of deleting several controls“, writes the researcher in the report.
The vulnerabilities were corrected immediately after the report was sent, on Monday, April 12, informed Fiocruz in a press release. On the report, “Hacker do Bem” insisted that the team responsible for developing Fiocruz’s systems should not be penalized for failures, as “failures happen and can be difficult to find”. He just asked for them to be corrected.
“I would like to ask for common sense and understanding from everyone. The technology department responsible for the system should not be ‘stoned’ and in no way penalized, as failures occur and failures like this can be difficult to find. I ask and just so that the faults are corrected“, he writes.
Official positioning
Although I fixed the vulnerabilities immediately after identifying the issues, the company recognizes the report’s legitimacy, but says that the database is actually a server in Rondônia for monitoring tests temperature of freezers and “is in the development phase, including using fictitious records in its database”.
“It is worth clarifying that the vulnerability found does not have any relationship with the information technology infrastructure of Bio-manguinhos, Fiocruz unit located in Rio de Janeiro and responsible for the production of the Oxford-AstraZeneca vaccine“.
“The Bio-manguinhos unit has a computational infrastructure intended exclusively for the production of vaccines, follows good national and international information security practices and undergoes frequent audits by several control bodies.“, writes a spokesperson for Fiocruz to The Hack, by email.
After the publication of the official positioning (saying that the server accessed was a testing service with false data), Hacker do Bem sent us images that indicate that the servers accessed are located in Rio de Janeiro and Manguinhos, cities where the production of vaccines against COVID-19 are concentrated. In addition, he ensures that it has found real employee data.
![Location of the IPs of the accessed servers, checked in the service "ipinfo[.]io", which mainly provides IP location information. Two IPs indicate that the servers are located in Rio de Janeiro and another in Manguinhos. Photo: Hacker do Bem.](https://impreza.com.br/wp-content/uploads/2021/04/1618843571_960_myanmar.png)
The process
The Hack managed, exclusively, an interview with the anonymous researcher responsible for identifying the vulnerabilities, to understand the process of identifying and producing the report until it was sent to Fiocruz.
He explains who started investigating Fiocruz systems for to be concerned about the waves of attacks against laboratories and pharmaceutical companies, mainly those related to research, development and production of vaccines against COVID-19.
“I started with an ‘information gathering’ collecting some information, such as ranges of IPs, domains, etc. Nothing much different than what should be done to map information. I used a script that I automated in python / shell script, at the beginning of the year, to identify open ports, services, domains, subdirectories, routes […] No state secrets so far. But during this analysis, I noticed some webservers, databases and APIs …“, it says.
Although the systems found had firewalls and other initial security tools configured, this firewall could easily be broken with bypass, that is, with techniques to bypass and bypass these surface safety tools.
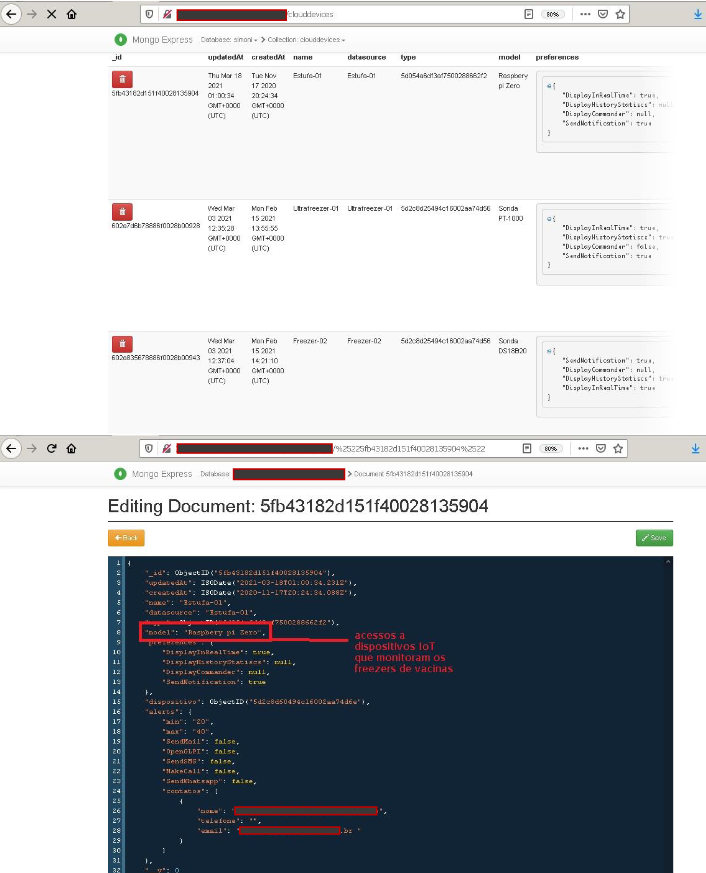
“I was quite frightened to see that the vulnerable service was directly linked to vaccine storage, equipment controls such as freezers, greenhouses, ultra-freezers, and some Internet of Things (IoT) devices that I believe are monitoring and alerting. ”
At this point, the researcher decided to organize a report and send it to the responsible company, since the information available there could cause a data leak and even a compromise in the production of vaccines and consequently bigger problems.
“It was a decision that made me lose sleep, I do not think it is legal to ‘point out’ flaws, and I do not even feel entitled to such action, to meddle in other people’s affairs, after all, nobody is perfect. But after what I saw, and knowing that it could create problems and affect the lives of many people, I entered a great ethical dilemma. I don’t know if it was the best decision, I even apologized to Fiocruz, but I thought it was the most correct thing to do“, comments on his reflections before sending the report.
After sending, the company returned saying that it blocked the exposures to the service and mitigated the failure that gave access to the elevation of privileges and lateral movement. They also thanked the researcher’s work for identifying and warning about the flaws. “Fiocruz was very competent. They were not negligent and the flaws were corrected quickly“, he comments.
However, the researcher does not believe in the official positioning of the company, which generated comments from angry internet users on stories from other portals. “Some may say that it is fakenews, others may say that it was a testing environment. I find it difficult, because they had real employee data, system logs since 2020. Who tests a system for that long? […] I know very well what I saw“, he explains.
It is important to remember that at no time was your goal to harm someone or cause any harm. Quite the opposite, the researcher appreciates Fiocruz’s work in the production of vaccines and asks the public to also respect them in this mission to save lives.
“The important thing is that the fault was corrected quickly and competently […] The idea here is not to point fingers, but to make a system that is so important for the population safer. After all, our lives depend on them. It is an important job and the cause is noble“, he concludes.
Source: TheHack