It was December 9, 1987. People flocked to department stores in search of ornaments and gifts for their loved ones. We were close to one of the happiest and most important celebrations in the world: the Christmas! Time to thank, get together with the family and warm up in front of the fireplace – of course, for countries that face winter during this time of year.
However, something strange was happening on other people’s computers. Some unlucky internet users started receiving emails from unknown recipients, having as their subject, the phrase “Let this exec run and enjoy yourself!” (or “Let this executable run and enjoy!”, in free translation). When running the CHRISTMA EXEC program, the user was viewing a Christmas tree in ASCII characters, along with the message “A Merry Christmas and my best wishes for next year”.
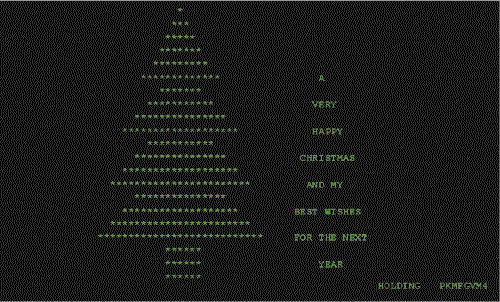
Cute, isn’t it? A pity that this “virtual Christmas card” was, in fact, the first Christmas malware recorded in the history of computing. It later became known as the Christmas Tree EXEC and, according to its creator – an anonymous student at the Clausthal University of Technology in Germany – was not designed for evil purposes. All he wanted was, in fact, to wish his friends a Merry Christmas.
It turns out that the way the program was designed, he automatically read the NAMES and NETLOG files (on which IBM computers stored his contacts) and sent the email automatically to his entire calendar. The networks of the time (like Bitnet) sent a message back to the sender for each file that passed over a node; depending on the amount of emails sent, the victim’s system froze quickly, preventing him from working.
Unpleasant gift
This is just one example of malware that spread during the Christmas season. As usual, cyber criminals like to explore holidays for the spread of phishing campaigns and malicious files. In 1999, for example, it was the turn of WM97 / Melissa-AG (also known as Prilissa) infect Microsoft Office Word documents, spreading via email.
The message – also from unknown senders – simply carried the message “This document is very important and you MUST read this!”. When opening the attached DOC, the payload was installed on the machine, remaining silent until December 25th. On that date, a cryptic message appeared in the form of a popup to scare the Internet user.
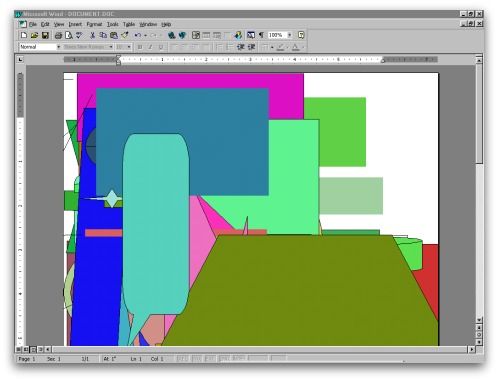
To make matters worse, colored blocks were randomly “painted” if you had Word open. Finally, unlike Christmas Tree EXEC (which did not cause much damage to the end user), Prillissa tried to format the hard disk’s root directory the next time the machine is turned on.
A “novelty”
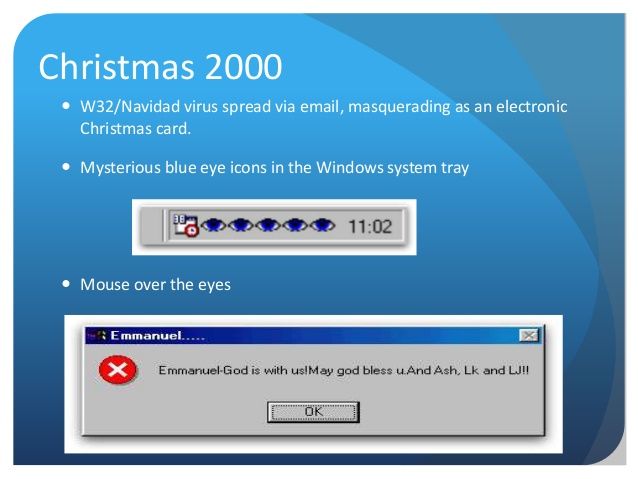
2000 was no different. The Christmas celebrations were interrupted by the W32 / Navidad – or simply Navidad -, which arrived via email disguised as a simple Christmas card. When opening the file, blue-eyed icons appeared in the Windows system tray, showing that the user had been infected; hovering over such icons would create popups with different messages mocking the Internet user.
Meanwhile, in the bowels of the operating system, Navidad altered several Windows registry keys, making it impossible to run any EXE files. To replicate itself, the malware used the MAPI32.DLL library and “sent itself” to the victim’s contact list.
Santa Claus or political activist?
Another supposed Christmas card that had an unpleasant surprise inside. In 2001, who attacked was the Maldal virus, which aimed to disseminate political ideals taking advantage of the commemorative date. The victim received, via email, a very affectionate message: “Hello! I can’t describe my feelings, but all I can say is happy New Year! ”. The first shots were detected around December 19.
When opening the Christmas.exe attachment, a Christmas card – very cute, by the way – was displayed on the screen, depicting Santa Claus in his sleigh. It turns out, under the hood, the virus altered Windows registry keys to start with the system, disabling the keyboard and deleting the entire Windows System directory. In addition, he also altered the Internet Explorer home page to display a website that criticized President George Bush.

As if that were not enough, when visiting the page in question, Javascript code was automatically executed, exploiting a vulnerability in Microsoft VM ActiveX to erase even more content from your hard drive. Maldal was able to infect even mIRC clients that were installed on the computer, sending the link to the malicious website whenever you entered a new room.
Chimney? No, back door
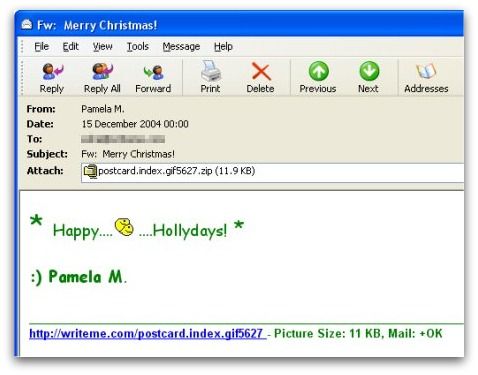
Some Hungarian funny guy fired, at Christmas 2004, the W32 / Zafi.D. He also landed in the victims’ email with a supposed Christmas card – the difference is that he had the ability to customize himself in different languages (Russian, Norwegian, Polish, German, French, Italian, Mexican, Spanish and even Portuguese), based on the victim’s email domain to be targeted.
Whoever opened the gift of evil would end up being infected with a payload that, in addition to exterminating security solutions (firewalls and antivirus), the Task Manager, Registry Editor and other crucial Windows features. Finally, a backdoor on port 8181 was created, but not for the entrance of Santa Claus, but for the execution of other malicious code.
For the naughty ones …
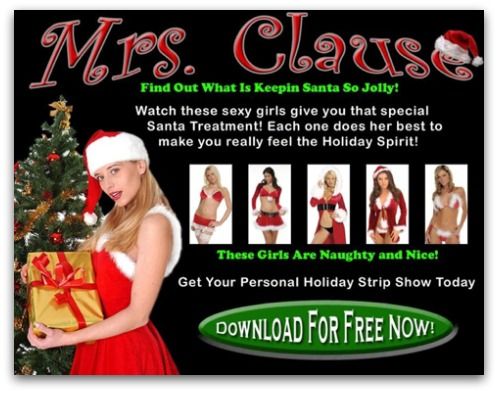
At Christmas 2007 a malicious campaign was also recorded, but it reached only the naughty ones who were interested in watching sexy videos of an actress dressed as Mrs. Claus. The email arrived with several suggestive subjects, including “Do you want to see something hot this Christmas?” and “Daddy said, Ho Ho Ho”. The messages were also varied, but all encouraged the user to click on the same link.
When you opened the website in question, you would see a page called “Mrs. Claus ”, who promised a free package of videos of models doing Christmas-themed strip tease. When you click the download button, however, what the user received was a copy of the W32 / Dorf-AE malware, which served as a gateway to other malicious packages and trojans.
Take care this Christmas!
There are several other campaigns that continued to be disseminated over the next few years – in 2012, for example, phishing used as a theme a supposed party invitation to infect machines with TROJ_ARTIEF.RTN, which exploited a vulnerability in Windows Common Controls to create a backdoor.
More recently, in 2014, another email campaign disseminated the MerryX, which disguised itself as a postcard to install a malicious payload capable of stealing data from the computer.
It is extremely common for criminals to take advantage of commemorative dates to deliver scams. So this Christmas, be very careful with promotions that seem too good to be true, be wary of emails with suspicious attachments or links (even if they are sent by contacts you know) and watch out for fake pages that simulate famous online stores.
The Hack wishes everyone a Merry Christmas!
See the original post at: https://thehack.com.br/especial-o-presente-que-voce-nao-pediu-ao-papai-noel-2/?rand=48873











