An attack involving Dropbox was in circulation in September. Researchers at Check Point Research (CPR) verified 5,550 such attacks in which hackers used the file hosting service to create fake login pages that eventually led to a credential harvesting page.
Dropbox phishing is yet another example of how cybercriminals continue to use legitimate services for business email compromise (BEC) attacks. “BEC 3.0 attacks refer to the use of legitimate websites, such as Dropbox, to send and host phishing material. The legitimacy of these sites makes it nearly impossible for email security services to stop them and for end users to detect them,” explains Jeremy Fuchs, cybersecurity researcher and analyst at Check Point Software for Harmony Email solution.
According to him, these attacks are on the rise and cybercriminals are using all your favorite productivity sites: Google, Dropbox, QuickBooks, PayPal and more. “It’s one of the smartest innovations we’ve seen, and given the scale of this attack so far, it’s one of the most popular and effective,” he says.
Below, Check Point Software researchers explain this attack, in which cybercriminals engage in social engineering with a Dropbox domain, designed to elicit a user response and trick the handover of credentials.
• Attack vector: Email
• Type: BEC 3.0
• Techniques: Social Engineering, Credential Collection
• Target: Any end user
Email example
This attack starts with an email coming directly from Dropbox.
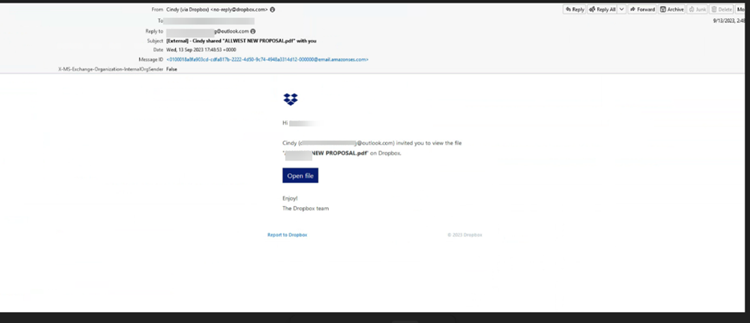
This is a standard email that anyone would receive from Dropbox, notifying them that there is a document to view. From there, the user is directed to a legitimate Dropbox page:

Although the content is that of a OneDrive-like page, the URL is hosted on Dropbox. When clicking on “Get Document”, the user is directed to the credential collection page.

This is the page hosted outside of Dropbox and where attackers want the user to click to steal their credentials.
Business email compromise has undergone a fairly rapid evolution. Just a few years ago, there was talk about so-called “gift card” scams. They were emails that pretended to come from a CEO or executive, asking a subordinate to buy “gift cards.” The idea is that cybercriminals would use the gift cards for personal gain. These emails typically came from spoofed Gmail addresses like CEO[@]gmail[.]com, not CEO[@]company[.]with.
It is also possible to see the representation of domains and partners, but these were always fakes, not real.
The next evolution came from compromised accounts. This could be a compromised internal user, such as someone in finance, or even a compromised partner user. These attacks are even more complicated because they come from a legitimate address. But the user may see a link to a fake Office 365 login page or an artificial language that NLP can understand.
Currently, what we see is BEC 3.0, which are attacks on legitimate services. NLP is useless in this case as the language comes directly from legitimate services and nothing is wrong. URL (web address) checking will also not work as it will direct the user to a legitimate Dropbox or other website.
These attacks are difficult to prevent and identify, both for security services and end users. Therefore, starting with education is essential. End users need to ask themselves: Do I know this person who is sending me a document? And even if the user clicks on the document, the next thing to ask: does a OneDrive page in a Dropbox document make sense? Asking these questions can help, as can hovering over the URL on the Dropbox page itself.
See the original post at: CisoAdvisor











