Researchers Tiago Assumpção and Robert Connolly, both from the American security company IOActive, identified a critical vulnerability in PJeOffice, software used by lawyers and judges from all over Brazil to digitally sign documents before sending them to the Electronic Judicial Process (PJe) platform – which, in turn, was created to unify the needs of the entire national Judiciary.
Investigations began in 2019, when lawyer João Falcão began testing the possibility of automating the use of the program to consult and analyze information on ongoing cases in courts across Brazil. It was identified, shortly after, that the update system used by the application has a loophole that can be exploited through a man-in-the-middle attack for remote code execution.
What happens is this: when opened, PJeOffice downloads a file via unencrypted HTTP to check for new updates. If so, a second package containing the update is downloaded automatically – again, without any kind of SSL or TLS encryption. That way, any attacker could intercept such communication and force the download of a malicious version of the program.
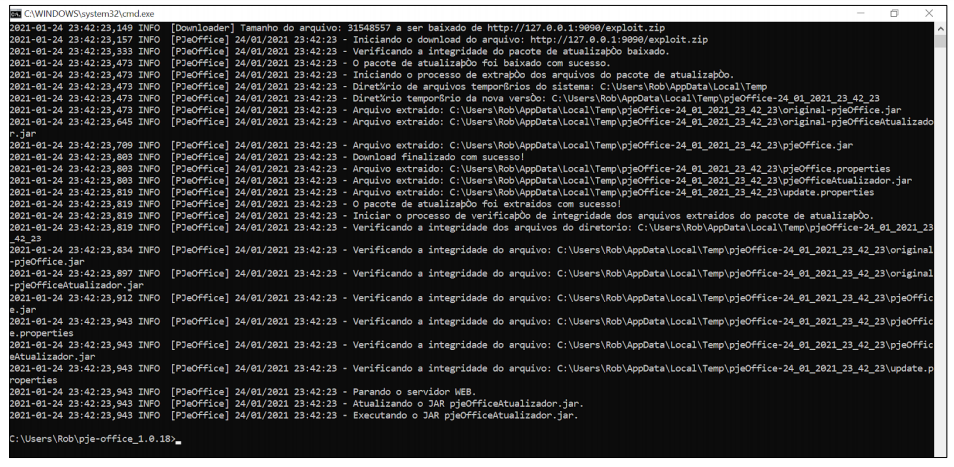
IOActive lists some scenarios in which this would be possible: in the use of open WiFi networks (cafes, restaurants, libraries, etc.), in ARF spoofing attacks, in DNS poisoning attacks and in situations in which the router, repeater or other infrastructure of the victim’s network component is previously compromised. All the criminal would need to do was change the legitimate URL used for the updates.
In a proof-of-concept (PoC), the researchers were able, in fact, to carry out such an intervention in the process and force the execution of random software on the PC. A malicious agent could, in the end, gain full control over the computer and the PJeOffice user account, potentially enjoying all your privileges as a member of the judicial ecosystem – even electronically sign documents.
Espionage, manipulation and adulteration
As well pointed out by the experts, the simple but very serious vulnerability would have the capacity to allow “government and industrial espionage, manipulation of the market, adulteration of legal processes, manipulation of the judicial system and breach of the chain of trust in democracy” Brazilian. PJeOffice has been around since July 2017, with versions for Windows, macOS, Debian and other Unix distributions.
After identifying and proving the vulnerability in partnership with João Falcão, IOActive reported the problem to the Pernambuco Court of Justice (maintainer of the software) and the problem was solved in build number 1.0.19. The Hack contacted the CNJ, but we did not receive a response until the end of this report; we will update the content as soon as the agency takes a position on the case.
Update: 03/02/2021, at 11:40 am
According to the CNJ, “The DTI / CNJ technical team has finished analyzing the report and concluded that it deals with version 1.0.18 of PJeOffice. The vulnerability pointed out has already been addressed in version 1.0.19 and, currently, PJeOffice is found in version 1.0.20 “.
Source: IOActive
See the original post at: https://thehack.com.br/vulnerabilidade-critica-e-identificada-em-software-do-conselho-nacional-de-justica/?rand=48873











