Software for administering web servers has been installed on more than 70 million domains; failure is serious, but it has already been corrected
A team of researchers at Digital Defense today announced the discovery of a security flaw that allows an evildoer to circumvent two-factor authentication (2FA) and gain access to a server managed by the cPanel & WebHost Manager (WHM) platform.
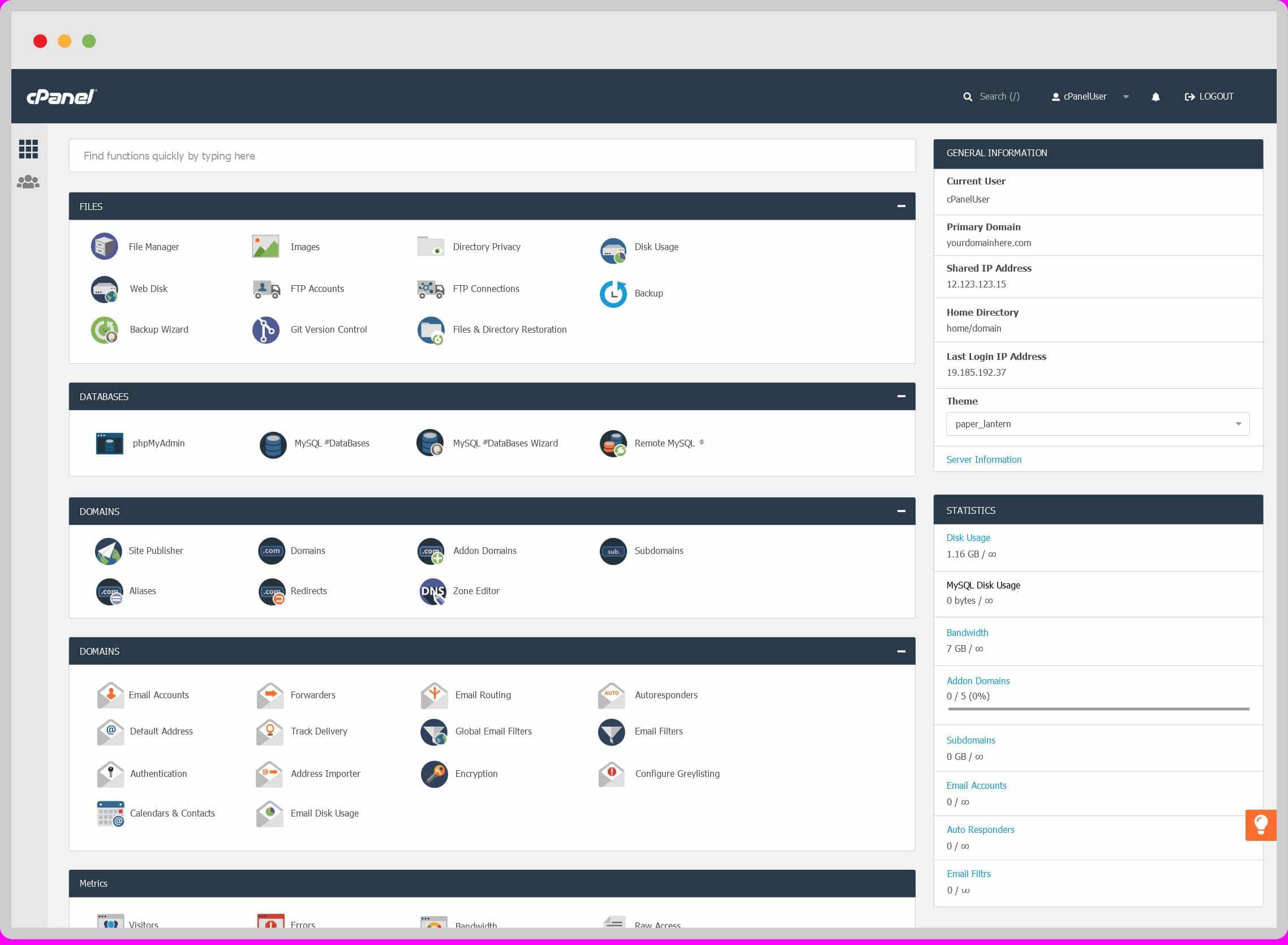
CPanel & WebHost Manager (WHM) is a set of tools used to simplify and automate tasks related to the administration of web servers. With more than 20 years on the market, the software has been used in more than 70 million domains to date.
According to Digital Defense, WHM’s authentication system is vulnerable to brute force attacks, allowing attackers in possession of valid credentials from an administrator or server user to guess login parameters and gain access without two-factor authentication. necessary.
CPanel is used to manage various aspects of a web server, such as hosted domains, databases, email accounts and more. Image: cPanel / Reproduction
The failure is serious, since 2FA was created precisely to prevent unauthorized access. The idea is that in addition to login and password, a user has to confirm a code, generated randomly and sent to a device they trust, before accessing the system.
The attack can be carried out “in minutes”, according to Digital Defense. The affected cPanel & WebHost Manager version is 11.90.0.5 (90.0 Build 5). According to cPanel, the company that develops the software, the problem was fixed in versions 11.86.0.32, 11.90.0.17 and 11.02.0.2.
“Our standard practice is to work together with organizations in a coordinated outreach effort to facilitate an immediate resolution for a vulnerability. Digital Defense VRT contacted cPanel, who worked diligently on a patch, “said Digital Defense.
Source: (https://olhardigital.com.br/)