QBot malware phishing campaigns have adopted a new distribution method using SVG files to perform HTML smuggling that locally creates a malicious installer for Windows.
This attack is made through embedded SVG files containing JavaScript that reassemble a Base64 encoded QBot malware installer that is automatically downloaded through the target’s browser.
QBot is a Windows malware arriving via a phishing email that loads other payloads, including Cobalt Strike, Brute Ratel, and ransomware.
SVG-based smuggling
HTML smuggling is a technique used to “smuggle” encoded JavaScript payloads inside an HTML attachment or a website.
When the HTML document is opened, it will decode the JavaScript and execute it, allowing the script to locally perform malicious behavior, including creating malware executables.
This technique enables the threat actors to bypass security tools and firewalls that monitor for malicious files at the perimeter.
Researchers at Cisco Talos observed a new QBot phishing campaign that starts with a stolen reply-chain email prompting the user to open an attached HTML file.
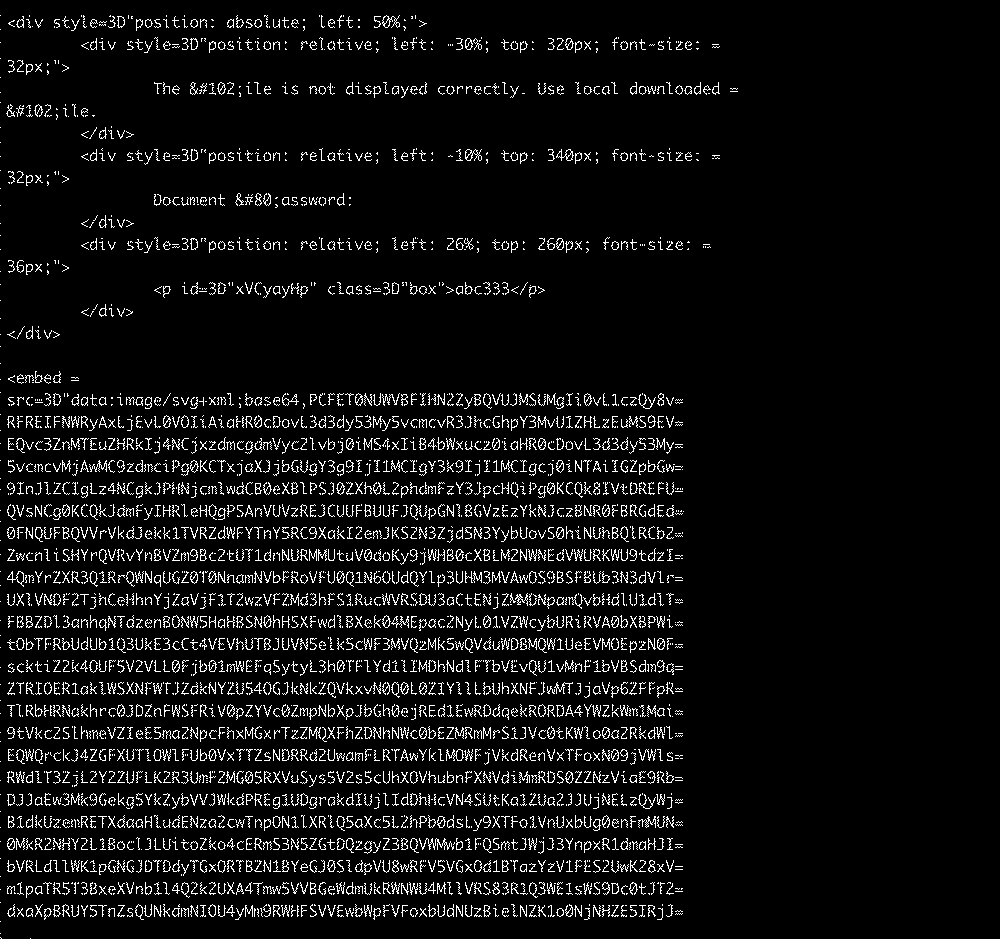
This attachment contains an HTML smuggling technique that uses a base64-encoded SVG (scalable vector graphics) image embedded in the HTML to hide the malicious code.
Base64-encoded SVG file inside the HTML (Cisco)
Unlike raster image types, such as JPG and PNG files, SVGs are XML-based vector images that can include HTML <script> tags, which is a legitimate feature of that file format.
When an HTML document loads an SVG file through an <embed> or <iframe> tag, the image will be displayed, and the JavaScript will be executed.
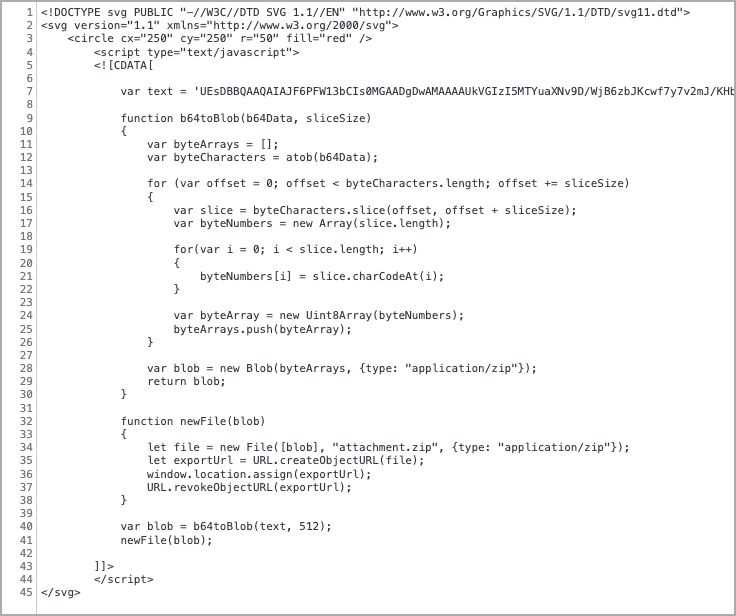
Cisco’s analysts decoded the JavaScript code in the SVG blob and found a function that converts an included JS variable ‘text’ into a binary blob, followed by a function that converts the blob into a ZIP archive, as shown below.
Deobfuscated JavaScript code (Cisco)
“In this case, the JavaScript smuggled inside of the SVG image contains the entire malicious zip archive, and the malware is then assembled by the JavaScript directly on the end user’s device,” explains Cisco.
“Because the malware payload is constructed directly on the victim’s machine and isn’t transmitted over the network, this HTML smuggling technique can bypass detection by security devices designed to filter malicious content in transit.”
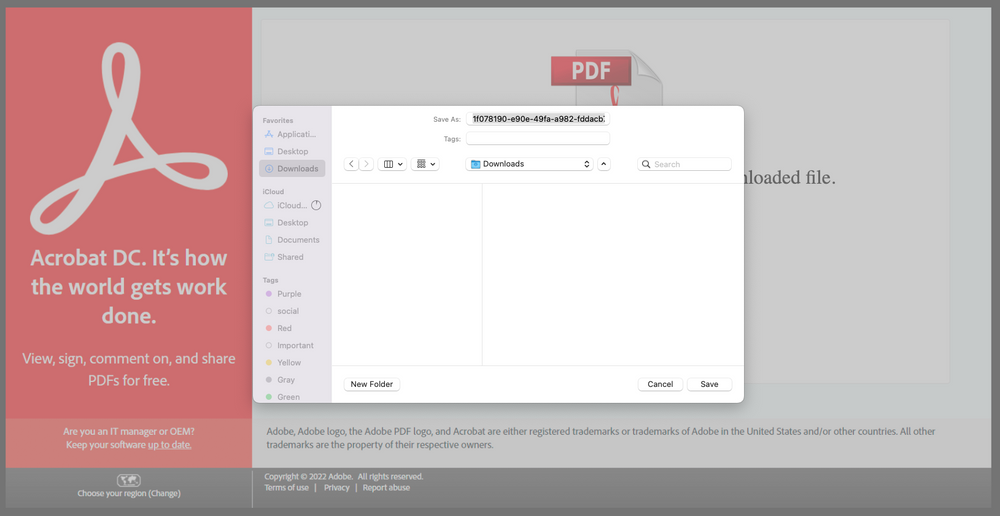
The downloaded archive is password-protected to evade scrutiny from AVs, but the HTML the victim opens contains the ZIP file’s password.
ZIP download dialog and fake Adobe HTML showing the password (Cisco)
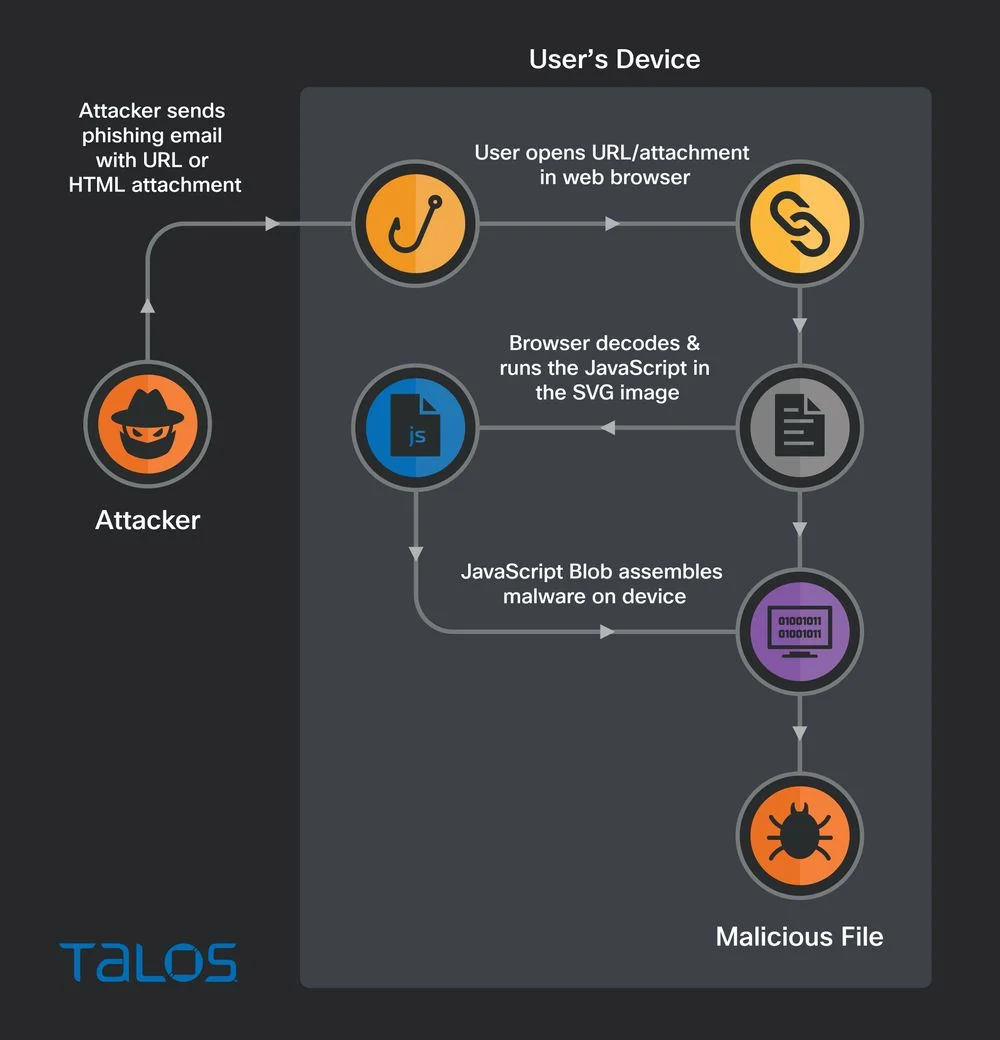
If opened, an ISO file is extracted on the victim’s machine that leads to a typical “ISO → LNK → CMD → DLL” infection or some variation of it.
It is assumed that using the SVG file to hide malicious code inside an HTML attachment helps further obfuscate the payload and increases the chances of evading detection
Infection chain (Cisco)
To protect systems from HTML smuggling attacks, block JavaScript or VBScript execution for downloaded content.
QBot recently exploited a Windows vulnerability that enabled its attachments to bypass Mark of the Web security warnings, but Microsoft fixed this yesterday with Microsoft’s December 2022 patch.
Source: BleepingComputer, Bill Toulas