Special Offer for Today only!
A newly discovered Linux malware, dubbed ‘DISGOMOJI,’ employs an innovative technique of using emojis to execute commands on infected devices, targeting government agencies in India.
The malware was discovered by the cybersecurity firm Volexity, which believes it is linked to a Pakistan-based threat actor known as ‘UTA0137.’
“In 2024, Volexity identified a cyber-espionage campaign undertaken by a suspected Pakistan-based threat actor, tracked by Volexity under the alias UTA0137,” the firm explains.
“Volexity assesses with high confidence that UTA0137 has espionage-related objectives and is tasked with targeting government entities in India. Based on Volexity’s analysis, UTA0137’s campaigns appear to have been successful,” the researchers continued.
The malware is similar to many other backdoors and botnets used in various attacks, enabling threat actors to execute commands, take screenshots, steal files, deploy additional payloads, and search for specific files.
However, its use of Discord and emojis as a command and control (C2) platform makes this malware distinctive and potentially able to bypass security software designed to detect text-based commands.
Discord and Emojis as a C2
According to Volexity, the malware was discovered after researchers found a UPX-packed ELF executable in a ZIP archive, likely distributed through phishing emails.
Volexity believes that the malware targets a custom Linux distribution named BOSS, used by Indian government agencies as their desktop. Nonetheless, the malware could just as easily be employed in attacks against other Linux distributions.
When executed, the malware downloads and displays a PDF lure, which is a beneficiary form from India’s Defence Service Officer Provident Fund in case of an officer’s death.
However, in the background, additional payloads are downloaded, including the DISGOMOJI malware and a shell script named ‘uevent_seqnum.sh,’ which is used to search for USB drives and steal data from them.
When DISGOMOJI is launched, the malware exfiltrates system information from the machine, such as IP address, username, hostname, operating system, and the current working directory, and sends this data back to the attackers.
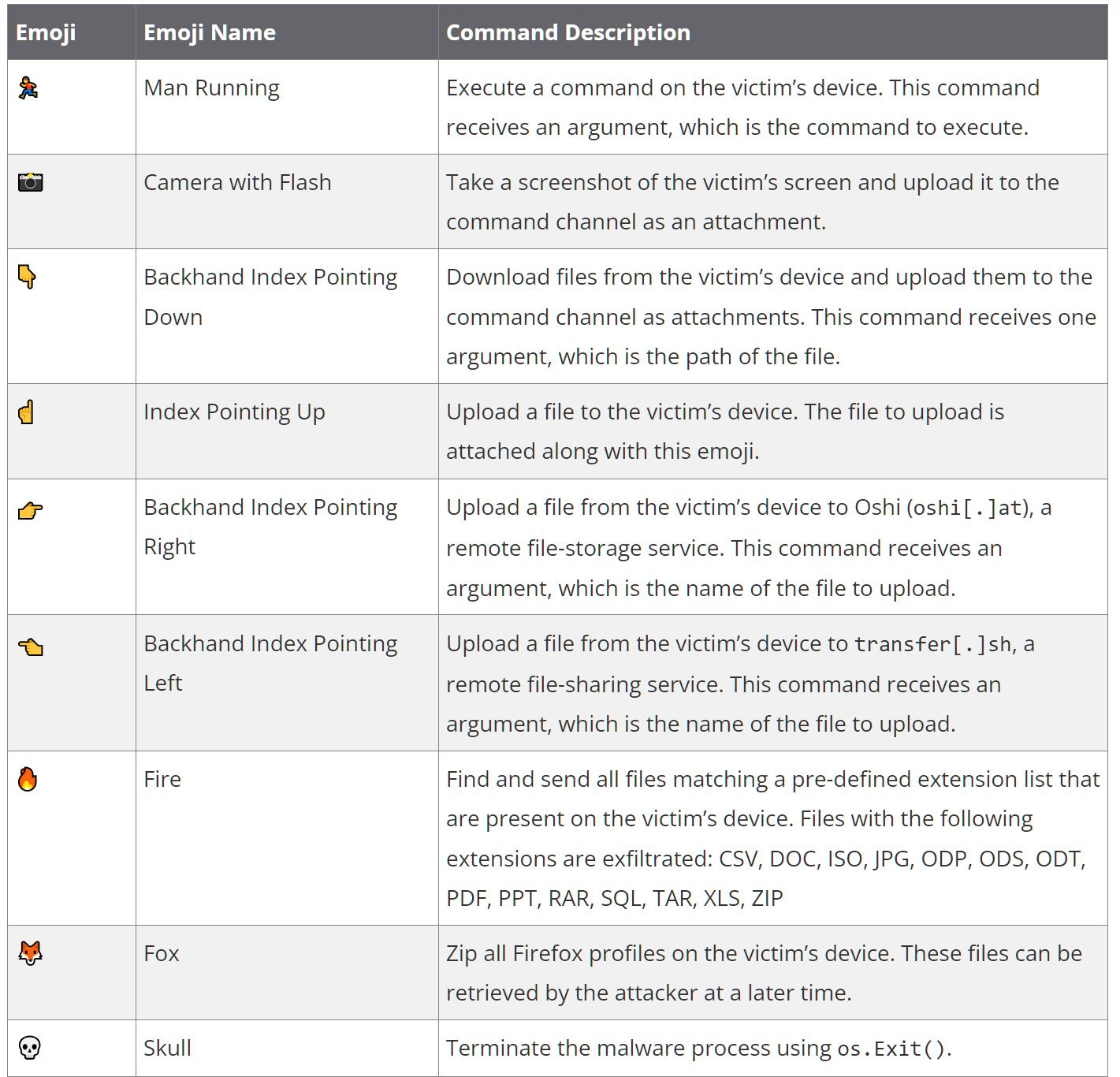
To control the malware, the threat actors use the open-source command and control project discord-c2, which utilizes Discord and emojis to communicate with infected devices and execute commands.
The malware connects to an attacker-controlled Discord server and waits for the threat actors to type emojis into the channel.
“DISGOMOJI listens for new messages in the command channel on the Discord server. C2 communication takes place using an emoji-based protocol where the attacker sends commands to the malware by sending emojis to the command channel, with additional parameters following the emoji where applicable. While DISGOMOJI is processing a command, it reacts with a “Clock” emoji in the command message to let the attacker know the command is being processed. Once the command is fully processed, the “Clock” emoji reaction is removed and DISGOMOJI adds a “Check Mark Button” emoji as a reaction to the command message to confirm the command was executed.” – Volexity
Nine emojis are used to represent commands to execute on an infected device, which are listed below.
The malware maintains persistence on the Linux device by using the @reboot cron command to execute the malware on boot.
Volexity reports that they discovered additional versions of DISGOMOJI and the USB data theft script that utilize other persistence mechanisms, including XDG autostart entries.
Once a device is breached, the threat actors use their access to spread laterally, steal data, and attempt to steal additional credentials from targeted users.
While emojis may seem like a “cute” novelty, their use could allow the malware to bypass detection by security software that typically looks for string-based malware commands, making this an intriguing approach.
Source: BleepingComputer, Lawrence Abrams